Application Security is one of the core aspects of cyber security which is not getting the attention it deserves. Many developers tend to focus on the aesthetics, functionality, and performance of their applications and this inevitably means deprioritizing cyber security. Application Security is the general practice of minimizing the vulnerabilities in your software, making it immune to a range of cyber threats. Every institution of economic and strategic importance today uses some software or application. Even the operating system and your home PC are a type of software.
Let’s talk about some of the advances that were made in cloud computing in the last few years. Some early examples can be way back in 1996 you may have seen cloud computing happen with Hotmail where everyone could use a web browser to check emails. Later Salesforce came up with a Customer Relation Management app (SaaS) which allowed people to log in and use a web page. The business app VMWare came along in 1999 and started doing virtual machines. Then in 2006 Amazon allowed people to rent servers on their systems.
Categories of Cloud Computing
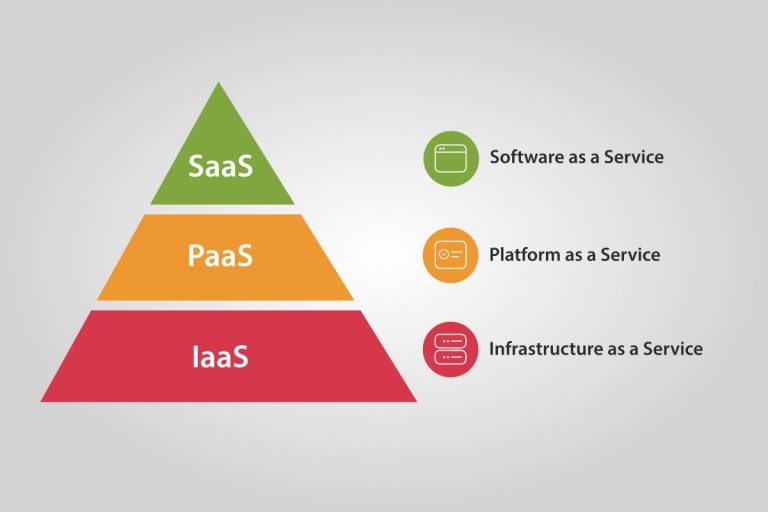
Failure to adequately protect the applications of your organization may result in loss of trust, brand image, and data. You can get exposed to huge penalties due to breaches of various regulatory frameworks. There are three different categories of what you would provide as a service in cloud computing that you must know of.
SaaS
This is called software as a service (SaaS). It is kind of like Hotmail, Gmail, or Office 365. Everything is provided through a web browser. Nothing to install you just use it. The Cloudnosys SaaS platform safeguards your cloud against vulnerabilities, provides total visibility, control over cloud security, and compliance in AWS, Azure, and Google Cloud Platform. Facebook, DropBox, and Google Docs are good examples of SaaS platforms.
PaaS
This is called platform as a service (PaaS). It is like renting a server and you install software on it. PaaS has been around for as long as there have been web hosting companies such as GoDaddy where you do not have to buy a server.
IaaS
This is called Infrastructure as a service which is a complete solution. This provides you with an entire network that is virtually hosted on somebody’s cloud. You get to have a virtual control panel and you would never actually have to install any wires or configure anything except through the virtual software portal.
Essential Cloud Service Characteristics
In Cloud Computing there are five essential cloud characteristics which are as follows:
On-Demand Self Service
It’s kind of like selecting things from a menu, we can say a vending machine or subscribing to a server service. Like in Azure, you can use their control panel and sign up for a server that is small and free to very real, robust, on-demand, and expensive.
Global Access
It costs a lot of money for a cloud company to develop because they have so many data centers around.
Shared Resource Pool
A massive data center is built and shared among thousands of customers. A large group of servers is shared among a group of clients.
Dynamic Growth
You can expand your service and shrink it depending on the needs of your current processes. If there is some new product or something new in the news that happens to be lucky to hit your company you don’t have to worry about purchasing servers that might sit idle in the future so dynamic growth is a key feature of cloud computing.
Measured Service with Pay Per Use
It’s like a measurement meter. How much are you going to pay based on how many users you get or how much traffic is hitting your website.
Security Pitfalls in a Hybrid Environment
The cloud environment where all of this runs on whether we are talking about Amazon, Azure, or Google. The actual cloud that is supporting your cloud application is a vector of attack. The single sign-on part of these systems called IAM would allow an attacker to access the environment that is controlling your environment. There certainly are people out there in businesses who have dedicated a hundred percent to one cloud platform or one technology stack but in practice, there are a lot of other things that tie into this. Third-party APIs like a platform called Lambda, a serverless environment in Amazon. There are integrations with third-party services like Zendesk. You have things like Github and GitLab. All of these things are other vectors into this environment because these do move at such a speed that you have to leverage a lot of these different APIs and other components into the environment.
The ability to actually monitor the data across all of the components is unique. It may spread across a lot of different components if we are dealing with sensitive data that’s personally identifiable information like personal health information or personal account numbers in the case of financial data. When it comes to the fact that the data itself is spread across shared storage and multiple volumes and that sort of things on the actual deployment side just having part of the security stack focused on code review and code testing in the continuous integration system doesn’t really give you much coverage.
Critical Application Migration Challenges
One of the ways that we deal with the speed problem or advantage is by building the security itself into the development and the operations process. When we are in a GitLab or GitHub environment, we are building applications in that space. We build the testing into our pipelines. It’s basically a way of automating a lot of the deployment steps testing, bundling deploying into the application before it is actually pushed into the cloud environment. Moving applications that are not built that way is in itself a fairly major task. You have to identify all the data points, where they come from, and where you can build these controls around them.
The various regulatory frameworks that handle this PCI, HIPPA, or GDPR, some of these may have conflicting requirements like stringent level of auditing. So, that alone can introduce some complexity to the way that this is done.
Application security is important because a hundred percent of applications today have some form of vulnerability. Security people are in demand and this skill set itself is not something where you’re going to show up with experience. Every day the security threat gets bigger and the number of people that handle that doesn’t really change. We grow a little but by no means do the humans scale to the level of threat as it stands. Globally gain visibility and control of all your security threats, vulnerabilities, configurations, risks, policies, and user activities with Cloudnosys. Our feature EagleEye dynamically remediates and heals your cloud using best practice standards to ensure compliance with little effort. We do not do things volume-based so there’s nothing feature restricted about a free trial. You can start your 14-day free trial today or check our pricing plan that is specially catered for your different needs.