Security and Automate Compliance
Avoid security drifts and ensure automate compliance with industry standards like PCI DSS, HIPAA, ISO, NIST, GDPR and many more.
Automate Compliance of Your Cloud and Container Infrastructure
AMAZING FEATURES
Risk Management
Compliance Assurance
Audit Management
Vulnerability & Remediation
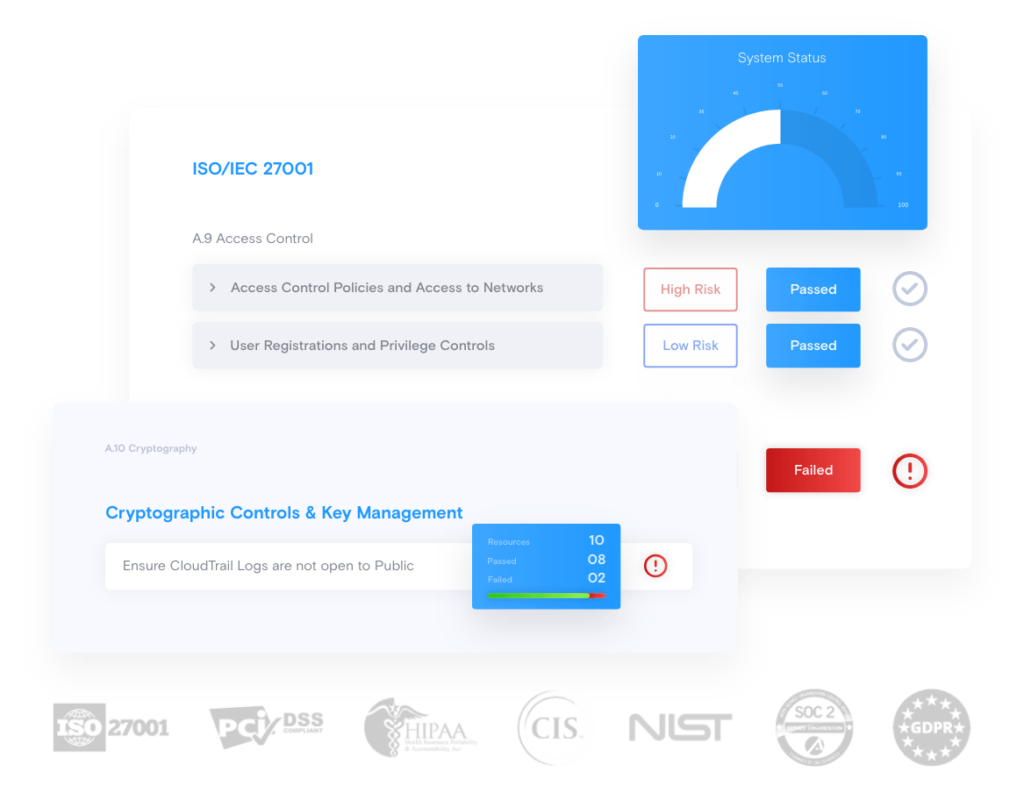
Ensure Infrastructure Compliance
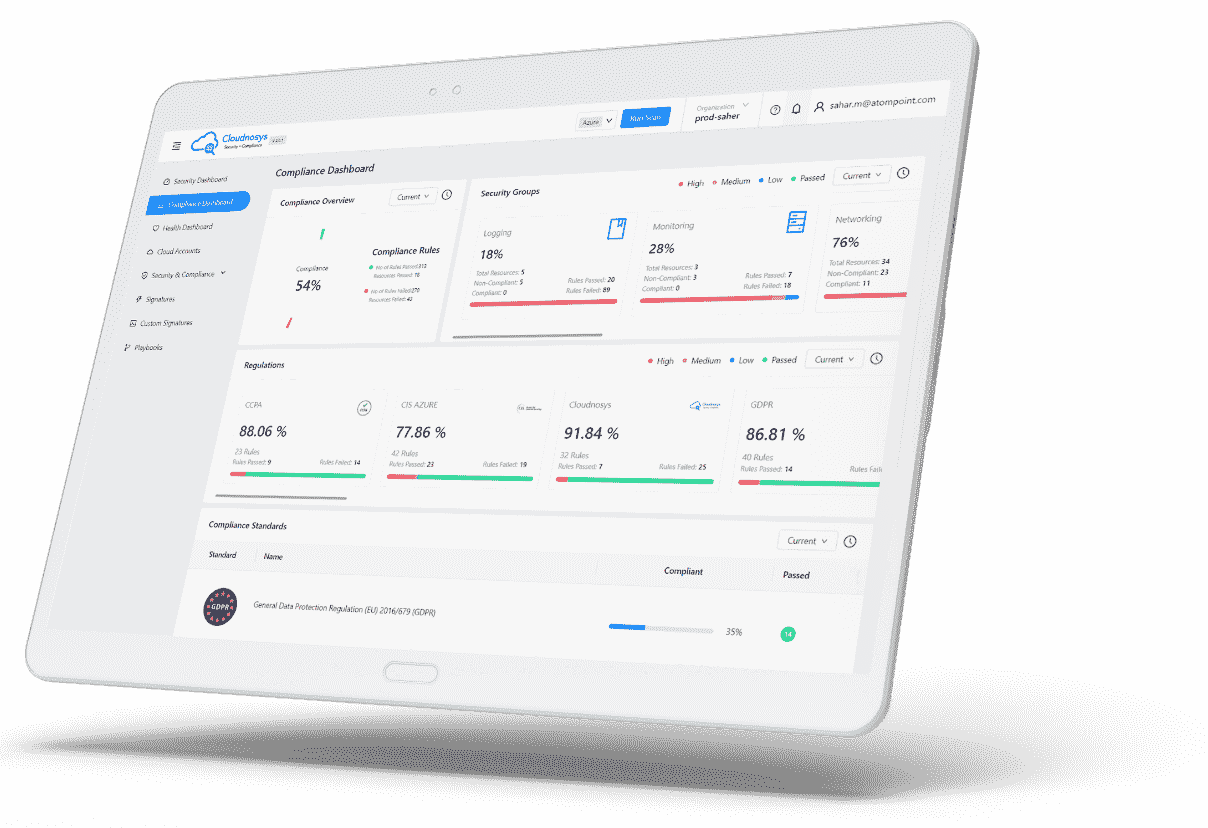
Visualize your compliance security and identify the critical risks for your business across all your cloud accounts, on one consolidated compliance dashboard.
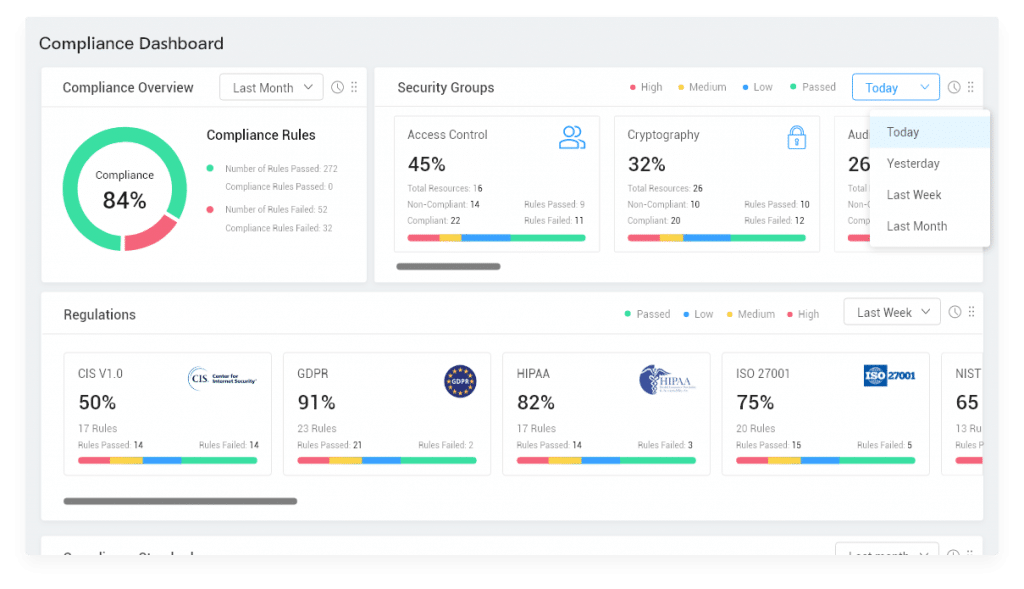
Elementary Security and Risk Management Across Multiple Regulations and Compliance Standards
CloudEye simplifies Regulatory compliance which involves a landscape of ever changing complex laws and standards. By levering our up to date comprehensive and cohesive set of control policies improves compliance posture and mitigates risk for compliance violations. Reduce compliance gaps and risk of audit failure by implementing proven best practices with pre-built policy engine.

The California Consumer Privacy Act (CCPA) rule reinforces security rights and buyer protection for the residents of California. CCPA ensures that organizations should have a business explanation behind the assortment of purchaser’s data.

(FedRAMP) is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.