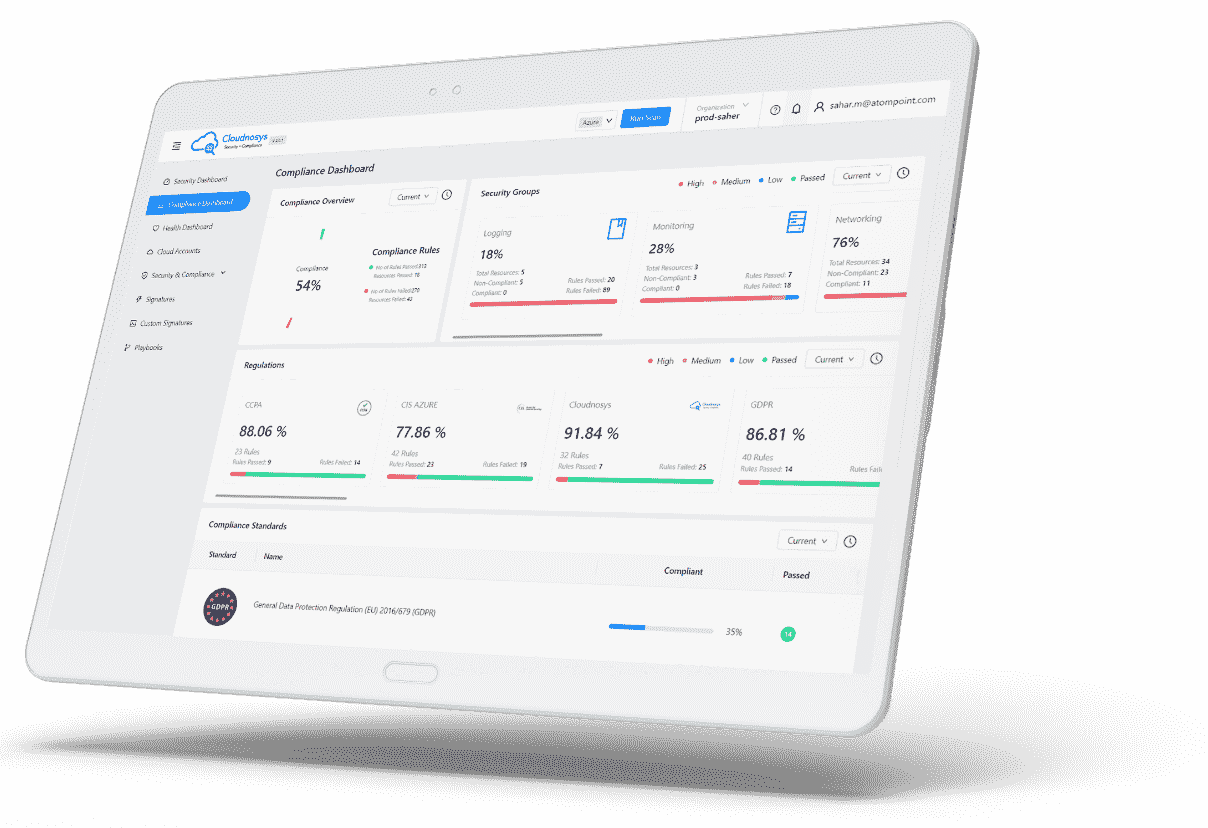
Improve Visibility, Continuous Security
Visibility of changes and user activity as they happen, across your entire infrastructure.
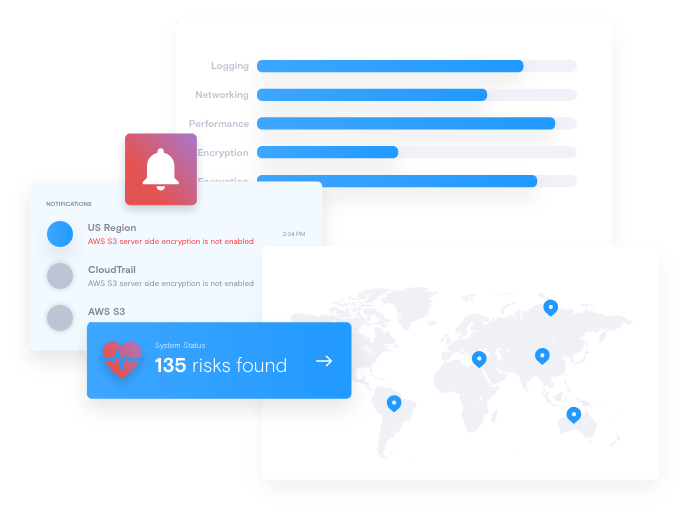
Enforce standards and improve visibility with continuous security posture
Rule your cloud with continuous deep visibility into your cloud accounts,
Rapidly improve visibility, continuous security, workloads, and microservices to give you complete security control.
Understand detailed mapping of all your services, networks, subnets, security groups and keys.
AMAZING FEATURES
Asset Discovery
Continuous automated asset discovery, and analysis for security. Complete discovery of security groups, configurations, and resources. Continuous scan of your infrastructure and identify which resources, ports, and protocols are at risk.
Configuration Management
Analytics around how the configurations are changing, full audit trail and control over baselines. Automated enforcement of baselines to eliminate drifts.Continuously monitors AWS configuration against regulatory requirements to streamline internal and external audits.
User and Permission
Enforce least privileges, eliminate unused security credentials. Continuous analysis and alert on security group changes and escalations. Simplify tracking of security groups and permissions.
Firewall Policy Management
Establishes policy guardrails and rapidly detect miss configurations and out of policy conditions for your firewalls, load balancers, WAF and much more. System recommends best firewall, encryption and ELB policies for specific compliance Regulations.
Complete Visibility
Visibility reveals operational risks by severity levels so you can prioritize remediation, Quickly improve visibility, and continuous security for your cloud. Having complete control of all global cloud infrastructure, security groups and networks.
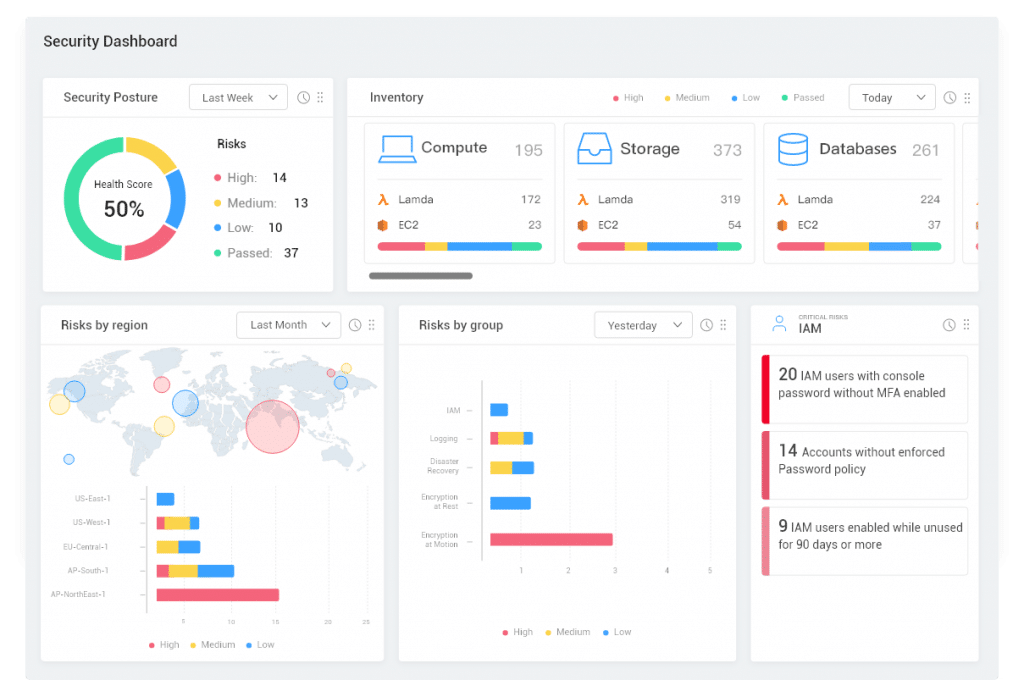
Security Scanning and Assessment
View and track all changes to your cloud environments, with the
details you need.
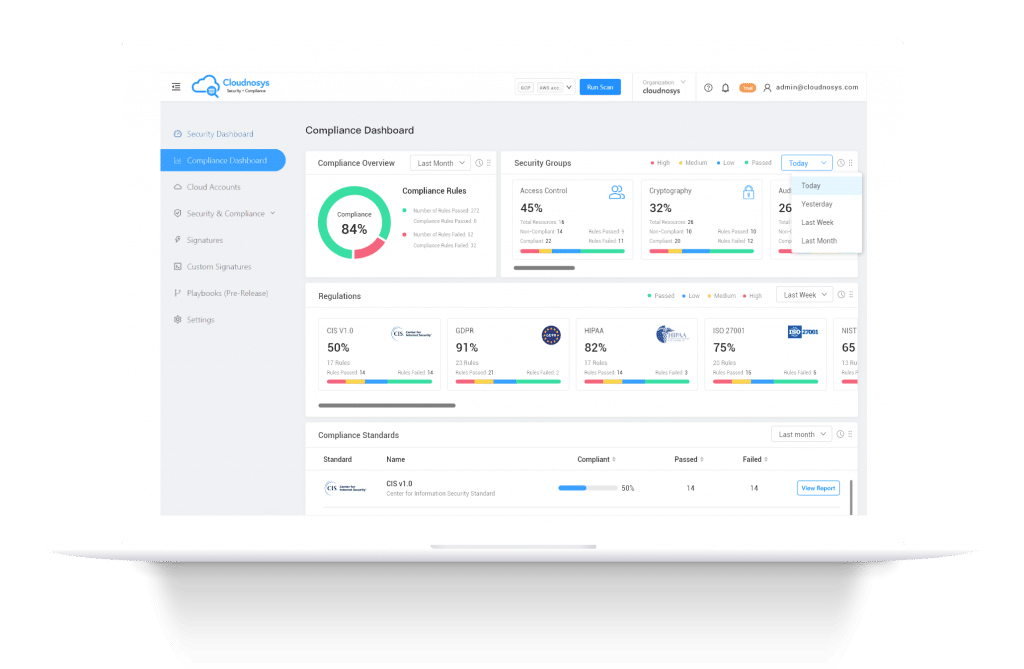
Identifying threats and vulnerabilities through real-time scanning and proactive monitoring. Visibility drives protection since you can’t protect what you can’t see.
We Help You To

Track additions, moves, drifts, and deletions in your environments

Identify gaps in network and service layers that could lead to a compromise

Get remediation guidance so you know what steps to take to eliminate your exposure
Highlight poor configurations which can lead to data loss