Release Notes #29- Version 3.4.0 (November, 2024) #
Exciting New Features and Improvements to Boost Your Cloud Security! 🚀 #
We’re thrilled to announce several updates and enhancements to Cloudnosys that take your cloud security and compliance to the next level. Here’s what’s new in Release 29 v3.4.0:
Affected Components: Scan Engine, Cloud View, CloudIQ, Add Cloud Account flow, Whole Platform, onboarding, Codebase, Risks page, Security Dashboard. Compliance Dashboard, Alerts.
🚀 New Features & Improvements #
1) Cloudnosys is Live on the GCP Marketplace! #
It’s official – Cloudnosys is now available on the GCP Marketplace! 🎉 Our platform for cloud security and compliance is now just a click away for GCP users. Get ready to integrate Cloudnosys and take control of your cloud security with ease.

2) Meet CloudIQ – Your AI-Powered Cloud Assistant #
Introducing CloudIQ, our brand-new Artificial Intelligence tool that connects to your AWS, GCP, or Azure accounts! 🧠✨
- CloudIQ uses CSPM scans to analyze your cloud resources in real-time.
- Ask CloudIQ any questions about your resources, risks, and compliance, and it’ll give you instant, actionable insights.
- It’s like having a cloud security expert available 24/7—ready to keep you informed and compliant with up-to-date reports.

Other Minor Improvements: #
1) Streamlined GCP Onboarding Flow #
Getting started with Google Cloud just got way easier! 🚀
Our new GCP Onboarding Flow makes adding your Google Cloud Platform account a breeze. The intuitive, step-by-step process ensures you set up everything quickly and correctly—without any headaches. You’ll be up and running in no time, securing your GCP resources with Cloudnosys faster and more efficiently than ever before.

2) EagleEye – Real-Time Threat Detection #
Stay on top of security with EagleEye, our real-time threat detection tool! 🦅💥
- EagleEye now tracks changes in your AWS environment (IAM, EC2, S3, and more) and instantly reflects them on your security dashboard.
- You’ll get near-instant alerts when something changes in your cloud account—helping you catch threats as they happen

Alerts for EagleEye on Platform:
Each alert displays the organization name, the cloud account affected, and the specific service (such as IAM, EC2, or S3) involved. The alerts are time-stamped for easy tracking.

3) Playbooks – One-Click Risk Mitigation #
Risk mitigation just became a one-click process with Playbooks! 🔧
- With new templates available, Playbooks can now be triggered automatically through EagleEye’s real-time scans.
- One click, and your cloud security threats are mitigated. Talk about simplicity and speed!

4) Signature Improvements #
We’ve updated our signature library to help you catch more threats across AWS:
- AWS Signatures:
- AWS: CF-001, CF-002, CF-003
- AWS: CLT-003, CLT-006, CLT-007
- AWS: CWALM-001, EBS-001, RDS-009
These improvements enhance detection, ensuring your cloud environment stays secure with the latest threat intelligence.
5) Expanded Compliance Reports #
We’ve added more signatures to strengthen our Compliance Reports:
- Cloudnosys Best Security Practice Compliance
- AWS CIS
- GDPR
- NYCRR (New York Codes, Rules and Regulations)
- Saudi NCA CC (National Cybersecurity Authority Critical Controls)
These additions ensure you stay on top of regulatory requirements and best practices for cloud security compliance.

🐛 Bug Fixes: #
- Timestamp Inconsistency: Resolved the timestamp mismatch issue between the Multi-Cloud Selector and the Cloud Accounts Page post-scan, ensuring data consistency across the platform.
- AWS Test Connection Errors: Fixed the errors related to AWS Test Connection API, ensuring smoother connections and fewer disruptions during testing.
- Signature Description in Critical Risks Widget: Addressed the issue where signature descriptions were undefined in the Critical Risks Widget, ensuring better visibility and clarity on identified risks.
- Run Scan Button Disabled: Fixed the problem where the Run Scan button remained disabled even when a non-running scan account was selected. Now, the button will enable appropriately based on account selection.
- User Invitation Input Box Reset Issue: Corrected the issue where the Input Box did not reset after inviting a user to the organization, improving user experience during the invitation process.
- Drawer Loading When Navigating Deeply in Resource Path: Resolved the issue where the drawer would keep loading when navigating through deep resource paths, ensuring smoother navigation.
- Missing Back Navigation & Breadcrumb Inconsistency: Addressed the missing back navigation and breadcrumb inconsistencies in the Security and Compliance Dashboards, improving overall navigation and user flow.
Release #28- , 2024 (version 3.1.5) #
At Cloudnosys, our goal has always been to provide our user with total control over their cloud security and compliance. We are thrilled to announce the release notes for Cloudnosys v3.0.11, a significant advancement in our objective to transform cloud security. This update significantly improves our platform.
Affected Components: Codebase, Alerts, Add Cloud Account flow, Cloudxray, Inventory page, Security Dashboard, risks page, Whole Platform, Scan Engine, Cloud Accounts pages, Drawer Resource, Compliance Dashboard, Custom Signatures, Standards
🚀 New Features & Improvements #
GCP Cloudxray #
🌟 Cloudxray – OS & Malware Scanning (CWPP) for GCP
Introducing Cloudxray, the groundbreaking agentless cloud workload protection platform (CWPP) by Cloudnosys, now available for GCP cloud accounts! Discover unmatched coverage and profound insights into your cloud workloads, including servers like Compute Engine and other virtual machine instances, all while eliminating performance impact, security concerns, and the burden of agent-related operational costs.
Cloudxray conducts thorough scans for Malware and OS Vulnerabilities on cloud configurations and identities through a unified platform and a cohesive data model, providing a comprehensive understanding of context and delivering prioritized alerts. Revolutionize your cloud security with Cloudxray and unlock a new level of protection like never before. 🚀🔒
For more details on Cloudxray, visit [Cloudxray on Cloudnosys]
Presets functionality #
🌟 Presets Functionality on Cloudnosys Inventory/Risks Page:
We are excited to introduce the new Presets functionality on the Cloudnosys Inventory/Risks page! This feature allows you to save your search queries for quick and easy access in the future. Whether you’re looking for specific risks by Risk Name, Risk ID, CVE Name, CVE ID, or other criteria, you can now save these search filters as presets.
With the Presets functionality, you can streamline your workflow by:
– Quickly applying previously saved search queries without re-entering the criteria.
– Managing your search queries with ease, saving time and effort.
– Customizing and saving multiple presets for different types of searches, ensuring you always have the right information at your fingertips.
Enhance your inventory/Risk management with this powerful new feature, making it simpler than ever to maintain visibility and control over your cloud security landscape.
For more details, visit [Cloudnosys]
Cloudview #
Cloudview, a graphical representation of your Cloud account resources, now available on Cloudnosys! Cloudview enhances your cloud management experience by providing a visual overview of your cloud environment. Let’s dive into its powerful features:
Cloud Account Selector:
Easily switch between different cloud accounts with the Cloud Account Selector. This feature allows you to manage and view multiple cloud environments seamlessly, ensuring you always have the right context for your security operations.
Graph Modify:
Customize and interact with your cloud resource graph through the Graph Modify feature. This tool lets you adjust the visual representation of your cloud infrastructure, making it easier to identify relationships and dependencies among your resources.
Query Presets:
Leverage the new Query Presets functionality to save and reuse your most frequent search queries. This feature streamlines your workflow by allowing you to quickly apply previously saved queries, saving time and effort in managing your cloud resources.
Tags:
Organize and categorize your cloud resources with Tags. Cloudview supports tagging for misconfigurations, CVEs, and malware, providing an organized and efficient way to manage your cloud security landscape. Tags help in quickly identifying and prioritizing critical issues, ensuring a focused and effective response.
Cloudview transforms your cloud management with a visual, intuitive approach, enhancing your ability to maintain visibility and control over your cloud security.
For more details, visit Cloudnosys
Other Minor Improvements #
Enhanced Risk Prioritization in the Critical Risks Widget #
the Critical Risks widget on Cloudnosys. This enhancement prioritizes services with the highest number of associated risks, marked with a warning sign for immediate alert. The widget categorizes risks into areas like Authentications, Data At Risk, Neglected Assets, OS Vulnerabilities, Vulnerabilities, Malware, IAM Misconfigurations, and Lateral Movement, displaying the most significant risks along with their severity, affected resources, and service type. This update helps you quickly identify and address critical security issues, making cloud security management more efficient.
OS version in the CSV of inventory #
We have implemented a minor improvement in the inventory data on Cloudnosys by removing the “OS Version” column from the CSV. This adjustment simplifies the data and enhances the focus on the most critical information relevant to your cloud resources. You can now view the updated inventory data with streamlined details for better clarity and management.
🐛 Bug Fixes #
Fixed: In the Compliance Report Drawer, we’ve corrected an issue where malware/CVE data incorrectly overrode signature data, ensuring accurate and reliable compliance reporting.
Fixed: We’ve addressed a bug that incorrectly categorized AWS ECS & ECR services under the ‘Other’ filter, now ensuring they are properly sorted and visible in their respective categories.
Fixed: The hover functionality in the Risk by Group widget on the Security Dashboard has been fixed to no longer stay static, enhancing user interaction and information display.
Fixed: Fixed the redirection issue in the Risk by Region widget, now accurately guiding users to the risk screen with appropriate high, medium, or low filters applied for improved risk assessment.
Release # 27 – March 25th, 2024 (version 3.0.1) #
At Cloudnosys, our goal has always been to provide our user with total control over their cloud security and compliance. We are thrilled to announce the release notes for Cloudnosys v3.0.11, a significant advancement in our objective to transform cloud security. This update significantly improves our platform.
Affected Components: Codebase, Alerts, Add Cloud Account flow, Cloudxray, Inventory page, Security Dashboard, risks page, Whole Platform, Scan Engine, Cloud Accounts pages, Drawer Resource, Compliance Dashboard, Custom Signatures, Standard
🚀 New Features & Improvements #
Selective Scan Scope #
We are excited to announce a new feature that significantly enhances the scanning capabilities within our cloud security platform. The Selective Scan Scope for Available Cloud Accounts allows users to tailor their security scans more precisely, aligning with their specific security needs and operational efficiencies.
The Selective Scan Scope feature introduces the flexibility to choose the scan target within your cloud environments. Users can now opt to scan for malware, CVEs (Common Vulnerabilities and Exposures), or both, based on their security priorities. This customized approach ensures a more focused security posture and offers cost-effectiveness and time efficiency by eliminating unnecessary scans.

How to Use the Selective Scan Scope Feature
- Initiate the Scan: Locate and click the Run Scan button on your cloud account’s security dashboard.
- Configure Your Scan: Upon clicking, a modal will appear on your screen presenting two checkboxes:
- Malware: Select this option to conduct a scan to identify malware within your cloud environment.

CVEs: Choose this option to scan for Common Vulnerabilities and Exposures (CVEs) that could affect your systems.

Auto Logout #
We’re adding an automated logout function to the Cloudnosys platform to improve security. Users will now be automatically logged out of accounts after a specified period of inactivity, protecting them and lowering the possibility of unwanted access. This update is a crucial component of our dedication to protecting your information and offering a safe, convenient experience. You will be shown this screen once you are auto-logged out of the platform.
Static Security & Compliance Dashboard Once the Organization has Expired #
Static Security and Compliance Dashboards are a new technique that we’re providing to the Cloudnosys platform for expired organizations. You can still access your previous Security and Compliance Dashboards in view-only mode even if your organization’s subscription has ended.
Until you renew your membership, these dashboards will remain static and only show you your most recent security and compliance status.
They won’t be interactive or updateable. This useful resource reminds you of the insights that Cloudnosys offers. To renew your subscription and resume full access to your cloud environment, please get in touch with Cloudnosys management or support.
Download the CSV file of inventory on the Inventory page for the Selected Cloud Accounts(s) #
Introducing the new download feature on the Inventory page! Now, Cloudnosys users can easily export a CSV inventory file for selected cloud accounts directly from the platform.
This enhancement provides a convenient way to access and analyze your cloud environment data offline. Whether you need to share insights with your team, conduct further analysis, or keep records for compliance purposes, downloading your inventory data is just a click away.
Dive into your Cloudnosys platform today to explore this feature and streamline your cloud management tasks. This is how your data will be shown in the CSV Format containing the Following Details of your Resources that are scanned by Cloudnosys.
Account ID- Cloud Account Name-Resource Name-Resource ID-Provider-Service-Region-VPC ID-Last Scanned-Tags-Misconfigurations-CVE-Malware-Third Party Risks-Total Risks
Other Improvements #
Filtered Inventory Data for CSV
Exporting your inventory to CSV now allows for filtered data selection, giving you tailored insights into your cloud resources.
AWS ID in Inventory CSV
Now, when exporting your inventory to a CSV file, you’ll find the AWS ID included for each selected account, enhancing traceability and account management.
Updated Overview Tab
We’ve streamlined the Overview tab by removing the Reconnect, Delete, and Force Clean-up buttons, focusing on a cleaner, more user-friendly interface. And moved it along to the configurations tab on the Edit Cloud Accounts Page.
CVE’s Score in Risks CSV
The CSV file from the Risks page now includes a CVE’s Score column, offering detailed insights into the severity of identified vulnerabilities for better risk assessment.
Disabled Add Cloud Account for Expired Organizations
For organizations with expired subscriptions, the “Add Cloud Account” button on the Security Dashboard is now disabled, ensuring clarity on subscription status and available actions.
🐛 Bug Fixes #
Fixed: In the Compliance Report Drawer, we’ve corrected an issue where malware/CVE data incorrectly overrode signature data, ensuring accurate and reliable compliance reporting.
Fixed: We’ve addressed a bug that incorrectly categorized AWS ECS & ECR services under the ‘Other’ filter, now ensuring they are properly sorted and visible in their respective categories.
Fixed: The hover functionality in the Risk by Group widget on the Security Dashboard has been fixed to no longer stay static, enhancing user interaction and information display.
Fixed: Fixed the redirection issue in the Risk by Region widget, now accurately guiding users to the risk screen with appropriate high, medium, or low filters applied for improved risk assessment.
Release # 26 – January 12th, 2024 (version 3.0.10) #
This release was a direct result of feedback received from valuable users. The new features & improvements are there to improve your experience better with Cloudnosys.
Affected Components: Cloudxray, Risk page, Inventory page, Alerts, Signatures, Emails, Risk Drawer, Resource Profile Drawer, Platform Header, Emails, Compliance Report Overview, and Add Cloud Account flow.
🚀 New Features & Improvements #
We’re excited to bring you a new update that enhances your experience on Cloudnosys! Here are the key features, improvements, and bug fixes in this release.
Download CSV Risks File From Risks Screen for Selected Cloud Account(s)
We’ve introduced a valuable enhancement based on user feedback. Now, you can download a CSV file of Risks for your selected cloud accounts, allowing offline access and efficient management of your Cloud Account Security.

Through this simple Download CSV button you can get all your information into your computer to work with it offline, below are the types of data you can get through our CSV File:
| ID | Service | Risk Type | Risk Severity | Risk Title | Affected Resources | Total Resources | First Seen | Last Seen | Suppression Status | Function | Security Group | Signature Title | Signature Pass Title | Signature Description |
Force Cleanup for Advanced AWS Cloud Accounts:
At Cloudnosys, we learn from our experiences with the users and provide them with ease, Another feature that we have introduced through user input is that You can use our “Clean Up Function” to clean out the scanners and resources that got stuck due to the clean-up option Failure in a rare case. this feature gives you the Authority in case of any problem to mitigate it by yourself just by clicking a button on the Edit Cloud Accounts page, This feature is only applicable once you receive an email from our platform and get the Alert in Alert system which states “The automatic cleanup function of the Cloudxray Scan feature did not execute as expected due to an unforeseen issue. To prevent you from incurring unnecessary costs”.

Other Improvements
Cost-Efficiency Boost with Lambda Function:
Bid farewell to lingering costs with our new Lambda Function. The Orchestrator now automatically turns on and off based on your scan needs, optimizing cost efficiency. Activate the orchestrator when you want to run a scan and turn it off once completed.
Show GuardDuty Risks on the Risk Pages:
Amazon GuardDuty risks, generated by its threat detection service, are now visible on the Cloudnosys Platform’s Risks screen. This provides a comprehensive view of potential threats in your AWS environment.
🐛 Bug Fixes #
We’ve resolved several bugs to enhance the reliability of Cloudnosys. Here are the notable fixes:
Fixed: In some cases whenever a Cloudxray Scan was Started or Completed there were multiple Alerts of starting & Completion of Scan.
Fixed: Addressed the issue of multiple alerts for starting and completing Cloudview scans in specific scenarios.
Fixed: Resolved continuous loading when clicking on the Resource Drawer in some Compliance Reports.
Fixed: Fixed the tab update issue for Custom Signatures when switching between organizations.
Fixed: Ensured proper tagging of Cloud Formation Templates (CFTs) in the platform’s Environments.
Fixed: Corrected the display of Malware and OS Vulnerabilities cards in the Critical Risks widget, showing the appropriate names of Standard
Fixed: Fixed the requirement to press the back button multiple times to navigate back from the Risks or Inventory page.
Fixed: Addressed the problem of all users receiving “New Security Risks Detected” emails when updating a cloud account name in specific organizations.
Fixed: Fixed missing Azure services logos in the Inventory widget on the Security Dashboard for certain scenarios.
Fixed: Resolved the issue where suppressed risks were disappearing from the suppression list in certain Cloud Accounts upon platform reload.
Thank you for your continued support and feedback. We hope these improvements make your Cloudnosys experience even better!
Release # 25 – December 6th, 2023 (version 3.0.8) #
This quick release was a direct result of feedback received from valuable users. The new features & improvements largely revolve around the way Cloudxray is used.
Affected Components: Cloudxray, Risk page, Inventory page, Alerts, Signatures, Emails, Risk Drawer, Resource Profile Drawer, Platform Header, Emails, Compliance Report Overview, and Add Cloud Account flow.
🚀 New Features & Improvements #
Enhanced Scan Progress Monitoring #
At Cloudnosys, we value our users’ feedback, and we’re thrilled to introduce a significant improvement to the scan progress monitoring experience. Based on your input, we’ve revamped the way you track not only the CloudEye scan but also the Cloudxray scan.

Efficient Cloudxray Scanning: Scan Running Instances only #
In response to valuable user feedback and to enhance both cost-effectiveness and efficiency, Cloudnosys is introducing a new configuration option for Cloudxray: “Scan Running Instances only.”
This adjustment not only reduces your costs but also accelerates the Cloudxray scan since less time will be spent.
Configuration during Cloud Account setup: You can now choose this configuration during the authentication step when adding a new Cloud Account with the Advanced protection level. By default, it’s selected to scan only running instances, offering a quicker and more cost-efficient process for first-time users.
Please note that this configuration will only be visible after you acknowledge that you have deployed the Cloud Formation Template in your AWS account.

Cloud Account Settings: For Advanced protection level AWS Cloud Accounts, this configuration is now available under the Configuration tab on the Edit Cloud Account page. Users can enable or disable it based on their scanning preferences.

Filter out Running Instances only #
Along with the update mentioned above, we’re introducing a handy addition to our Inventory page: filter “Running Instances only”.
- Streamlined Viewing: Easily separate running instances from stopped ones for clearer resource management.
- Effortless Transition: Cloudxray Scan system alerts for running instances will now take you directly to the filtered view.
- Focused Functionality: This feature is exclusive to relevant Cloudxray Scan system alerts, making resource management a breeze.

Other Improvements #
- Cost-Efficiency Boost with Cloudxray: Say goodbye to lingering storage costs. With Cloudxray’s latest updates:
- Snapshots and AMIs are removed right after volume creation.
- Volumes are now instantly deleted after being unmounted.
- Reliable Cleanup Alerts
- Rest easy with Cloudxray. In the rare event that the Cleanup function doesn’t run as expected, we’ve got you covered.
- Receive instant System Alerts and Emails, ensuring swift action from both you and our dedicated Cloudxray team. Your cloud security remains our top priority
🐛 Bug Fixes #
In our continued effort to make Cloudnosys the most reliable security platform, we successfully eliminated a handful of bugs!
Here’s a quick rundown on some of the fixes:
Fixed: In some cases whenever a user successfully updated the name of one of their GCP cloud accounts, some users of the Organization received an email regarding a permissions error.
Fixed: After successfully upgrading an AWS cloud account from Basic to Advanced protection level, the UI was still showing the protection level stated as Basic in rare cases.
Fixed: When a user clicked on a Cloudxray Scan system alert of a deleted cloud account while viewing any other cloud account’s settings, the user got redirected to a 404 page. Now a notification will pop up stating that the cloud account is no longer present and the user will stay at the other cloud account’s settings page.
Fixed: When a user clicked on a Cloudxray Scan system alert of an inactive cloud account, the user received a notification saying that the cloud account was no longer present. Now the notification clearly states that the cloud account is inactive instead.
Fixed: Some notifications related to Cloudxray Scan system alerts were popping up from the top-right of the screen instead of the bottom-right.
Fixed: Some signature cards were showing the title of their corresponding risks instead of the signature.
Fixed: For specific resources, the First Seen timestamp of their risks was showing the timestamp of Last Seen and vice versa.
Fixed: The Cloudxray Scan was not getting initiated right after the successful reconnection of an AWS cloud account with the Advanced protection level.
Release # 24 – September 22nd, 2023 (version 3.0.1) #
This mini-release was mainly aimed at resolving user experience issues. It was prioritized right after our last major release
Affected Components: Security Dashboard, Compliance Dashboard, Alerts, Cloudxray, Cloud Accounts page, Inventory page, Custom Signatures, Risks page, Suppression, and Signatures.
🚀 Improvements #
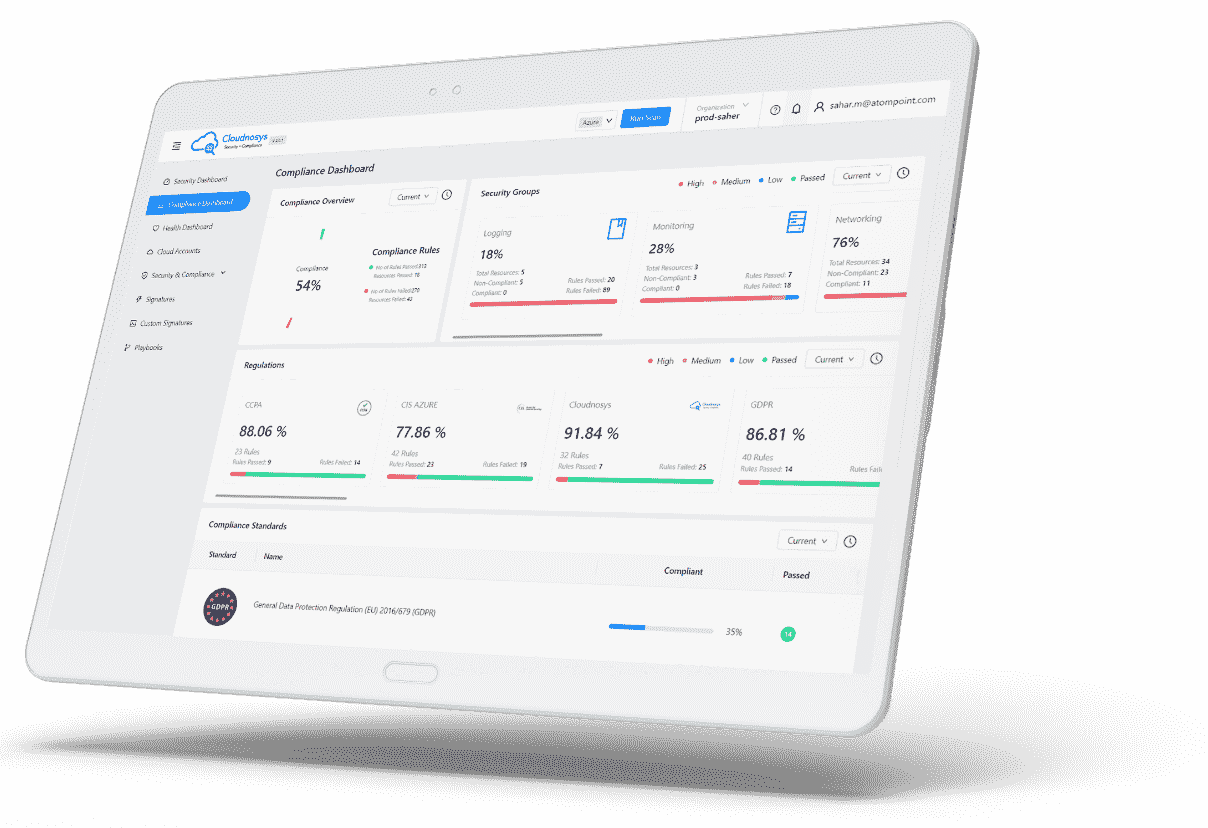
Revamped Security Groups widget #
Introduce the all-new Security Groups widget on the Compliance Dashboard, revamped to provide you with a more insightful and user-friendly experience. We’ve addressed the issues, making it easier than ever to assess and manage risks according to security groups effectively.

- Informative Metrics: Now you can gain deeper insights into the security status of your resources with the new metrics:
- Resources at Risk: This metric displays the number of risks associated with resources within each Security Group. We have refined the counts to accurately reflect your risk exposure.
- 1 risk on 1 resource counts as 1 risk,
- 1 risk on 2 resources counts as 2 risks,
- 2 risks on 1 resource count as 2 risks, and so on.
- Passed: Track the number of risks that do NOT exist on your resources. The counts have been improved to provide you with a precise overview.
- 1 passing signature on 1 resource counts as 1 risk passed,
- 1 passing signature on 2 resources counts as 2 risks passed,
- 2 passing signatures on 1 resource count as 2 risks passed, and so on.
- Refined Health Percentage: Understand the health of your selected cloud account(s) with a clearer health percentage calculation = 100 * Passed / (Passed + Resources at Risk)
- Resources at Risk: This metric displays the number of risks associated with resources within each Security Group. We have refined the counts to accurately reflect your risk exposure.
- Linked to the Risks page: Clicking on any Security Group will now take you to the Risks page with the filter of that Security Group applied.
With these improvements, the revamped Security Groups widget empowers you to make informed decisions and enhance the security of your cloud environment.
Interactive & More Insightful System Alerts of Cloudxray #
System Alerts of active cloud accounts from Cloudxray will now provide more information if you click on them. This will allow users to make relevant decisions without switching away from the platform and checking the emails.
Clicking on the system alert will pop up a modal with the same information that gets displayed in the detailed email that users receive when a Cloudxray scan begins and/or ends.
Additionally, from the same modal, you can also go to the Risks page or the Inventory page with all the relevant filters applied. This will save you time since you would not have to manually filter for (i) the resources that Cloudxray scanned, or (ii) the risks that Cloudxray detected.
🐛 Bug Fixes #
In our continued effort to make Cloudnosys the most reliable security platform, we successfully eliminated a few bugs on the platform!
Here’s a quick rundown on some of the fixes:
Fixed: Notifications from Cloudxray Scan alerts were sliding in from the top-right corner of the screen instead of the bottom-right corner.
Fixed: Custom Signatures were being displayed under the Signatures tab of the Risks page as well. Now they will only be displayed under their respective Custom Signatures tab.
Fixed: While creating a new Custom Signature, the ‘Risk Type’ field allowed selection of the types ‘Malware’ and ‘OS Vulnerabilities’ as well. Now the field will only show misconfiguration risk types as intended.
Fixed: While creating a new Custom Signature, the ‘Group’ dropdown field was listing the names of Security Groups.
Fixed: In the Inventory Summary widget on the Security Dashboard, the “Publicly Accessible” text was not formatted in one single line.
Fixed: Suppressing any resource was suppressing all the risks.
Fixed: When no cloud account was selected, the Signatures were not being displayed under the Signatures tab on the Risks page. Unlike risks, Signatures are independent of cloud accounts so now they are being displayed irrespective of cloud account selection.
Release # 23 – August 22nd, 2023 (version 3.0.0) #
Our mission at Cloudnosys has always been to empower businesses to maintain complete control over their cloud security and compliance. We’re excited to present the release notes for Cloudnosys v3.0, a major milestone in our journey toward revolutionizing cloud security. This update brings remarkable advancements to our platform, merging CWPP and CSPM capabilities seamlessly, and empowering organizations with unparalleled control plus comprehensive security measures for their cloud infrastructure.
New Components: Cloudxray, Risks page, Inventory page
Affected Components: Scan Engine, Security Dashboard, Access Control, Cloud Accounts, Drawers
🌟 Cloudxray: OS & Malware Agentless Scanning (CWPP) #
Introducing Cloudxray, the groundbreaking agentless cloud workload protection platform (CWPP) by Cloudnosys! Discover unmatched coverage and profound insights into your cloud workloads, encompassing servers like VMs and EC2 instances, all while eliminating performance impact, security concerns, and the burden of agent-related operational costs.

Cloudxray conducts thorough scans for Malware and OS Vulnerabilities on cloud configurations and identities through a unified platform and a cohesive data model, providing a comprehensive understanding of context and delivering prioritized alerts. Revolutionize your cloud security with Cloudxray and unlock a new level of protection like never before. 🚀🔒
For more details on Cloudxray, go to https://cloudnosys.com/cloudxray

🌄 The multi-purpose Risks page #
Previously, users didn’t have a centralized view to monitor all risks in one place. With the introduction of our new dedicated Risks page, you now have a comprehensive space to easily access Risks, Signatures, and Custom Signatures.

To further streamline your experience, all three tabs within the Risks page feature a convenient search and filter bar. This empowers you to quickly locate specific risks or apply custom filters to narrow down the results, ensuring efficient risk management and easier navigation.
Advanced Search & Filter #
We understand the importance of efficient risk management, and that’s why we’ve equipped the Risks page with powerful search and filter capabilities to streamline your workflow.
With the new Search Bar, you can quickly locate any specific risk or signature by simply entering its name or ID.

Additionally, our intuitive Filter dropdown empowers you to narrow down risks and signatures based on various criteria. Choose from a range of options, including:
- Cloud Provider (AWS, GCP, Azure),
- Severity (Critical, High, Medium, Low),
- Services,
- Risk Type, and
- Data Sources (Cloudnosys built-in Signatures, Cloudxray, and 3rd-party sources).
Effortlessly customize your risk view to focus on the areas that matter most to you.
Explore and Manage Risks with Ease: Tabs, List View, and More #
Under the Search & Filter bar, you will find 3 tabs – namely Open Risks, Signatures, and Custom Signatures.
1. The Open Risks tab #
The Open Risks tab displays all types of risks (Malware, OS Vulnerabilities, and Misconfigurations) associated with the cloud accounts selected.
This page directly enables you to proactively address vulnerabilities and make informed decisions to strengthen the security of your cloud infrastructure.
2. The Signatures Library tab #
Instead of going to the Signatures page, now you can just select this tab and go through all the signatures that CloudEye protects your cloud accounts with.

This tab will display all the misconfiguration checks the platform performs, no matter which cloud account is selected.
3. The Custom Signatures tab #
Instead of going to the Custom Signatures page, now you can just select this tab and go through all the signatures that you created yourself. Click on the “Add New Signature” to create new ones as usual.

Honorary Mention: List View #
Switch between Grid View and List View for a flexible risk management experience. The List View offers a streamlined, vertical format for easy scanning, quick identification, and efficient navigation. We aim to enhance your experience with a customizable interface that caters to your preferences and workflows.

🔥 Detailed Risk Profile #
Cloudnosys always had a Drawer showing details of each selected misconfiguration individually. We call this the Risk Drawer. But what good would be a Risk Drawer if it doesn’t show off the platform’s latest CWPP capabilities?!
That’s why we’ve taken our Risk Drawer to the next level, showcasing the platform’s latest CWPP capabilities like never before!
Risk Profile for OS Vuls #
When it comes to OS Vulnerabilities, our enhanced Risk Drawer goes above and beyond. It now displays valuable information about the specific CVE, giving you a quick glance at the details that matter. Take a look at the image below for a sneak peek.

Plus, we’ve added a convenient link in the drawer that allows you to explore further information about the CVE on NVD!
Risk Profile for Malware #
For Malware, we’ve taken things even further. Not only do you get additional details about the specific Malware, but we also provide a link that leads to more information on Virus Total.
WAIT -that’s not all: you can now precisely pinpoint where the Malware is located on your resources! Check out the GIF below to see it in action.

🧇 The brand-new Inventory page #
We are thrilled to unveil the all-new Inventory page, designed to provide you with a comprehensive view of all the resources across your multiple cloud accounts. Gone are the days of navigating through drawers; now, you have a dedicated page solely focused on empowering you with complete visibility and control over your cloud resources.

Uncover Risk Trends in Resources: The Upgraded Resource Drawer #
With the upgraded Resource Drawer, you’ll now find a dynamic health trend chart that tracks the number of risks associated with the resource over the last 7 days. Gain valuable insights at a glance and track the resource’s risk landscape over time.

But that’s not all – we’ve expanded the risk table within the drawer to include not only misconfigurations but also Malware and OS Vulnerabilities. Enjoy a comprehensive view of potential risks, enabling you to proactively address threats and fortify your cloud infrastructure.

✨ New Widgets on the Security Dashboard #
Instant Resource Insights: Inventory Summary widget #
Our new Inventory Summary widget in the Security Dashboard offers a holistic view of your cloud resources, providing valuable information at a glance. With this widget, you can effortlessly assess the overall status of your resources and make informed decisions to strengthen your cloud security.

Key features of the Inventory Summary widget include:
- Total Number of Resources: Get an overview of the total count of resources in your cloud environment.
- Number of Safe Resources: Identify the number of resources categorized as safe, ensuring a secure foundation for your cloud infrastructure.
- Number of Resources at Risk: Quickly identify the number of resources that are currently at risk, enabling proactive risk mitigation.
- Number of Publicly Accessible Resources: Understand the scope of publicly accessible resources, ensuring proper security measures are in place.
- Donut Chart: Visualize the proportion of Safe Resources and Resources at Risk, providing a clear understanding of the overall risk landscape.
- Number of Resources by Service Type: Gain insights into the distribution of resources across different service types.
- Resource Service Type Count Bar: Visualize resource distribution by service type, enabling efficient prioritization and optimization.
- Trend Graph: Track the number of resources over the last 7 days, helping you monitor resource growth and identify any anomalies.
With the Inventory Summary widget, you have a comprehensive overview of your cloud resources, allowing you to prioritize actions, mitigate risks, and maintain a robust cloud security posture. Explore the widget and unlock a new level of visibility and control over your cloud environment.
Quick Risk Insights: The Risks Summary widget #
The new Risks Summary widget in our Security Dashboard empowers you with a comprehensive overview of the risks associated with your cloud resources. With this widget, you can quickly assess the risk landscape, prioritize actions, and fortify your cloud security with confidence.
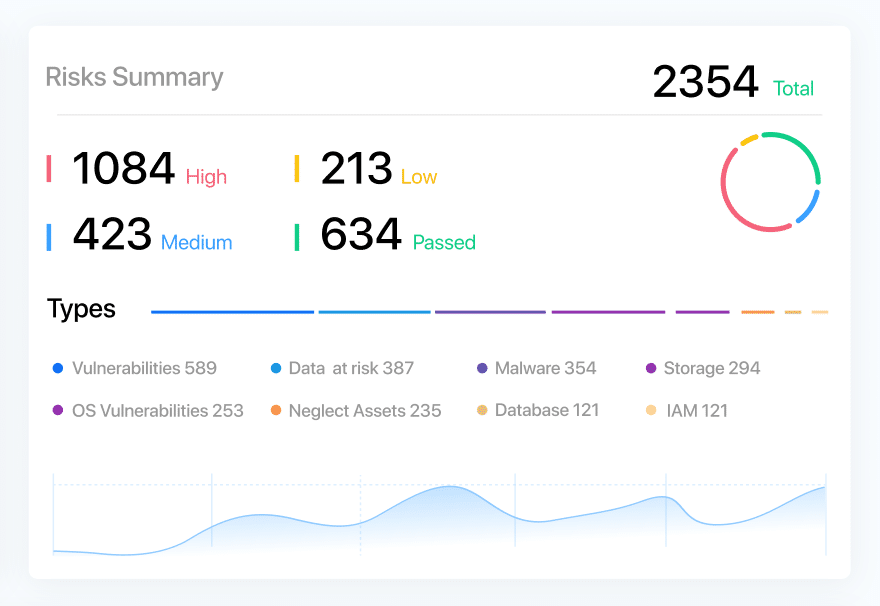
Key features of the Risks Summary widget include:
- Total Number of Risks in All Resources: Get a consolidated count of all risks across your cloud environment, enabling you to gauge the overall risk exposure.
- Number of Risks by SeverityType: Understand the distribution of risks by severity levels, allowing you to focus on critical areas that require immediate attention.
- Donut Chart: Visualize the proportion of risks divided by varying levels of severity, providing a clear understanding of the risk distribution and helping you prioritize mitigation efforts effectively.
- Number of Risks by Risk Type: Gain insights into the distribution of risks across different risk types, enabling you to address vulnerabilities specific to your environment.
- Risk Type Count Bar: Easily identify the proportion of each risk type through a visual bar, assisting you in identifying areas of concern and prioritizing risk mitigation strategies.
- Trend Graph: Track the number of risks over the last 7 days, empowering you to monitor the risk trend and identify any emerging patterns or potential vulnerabilities.
The Risks Summary widget offers a concise yet comprehensive snapshot of the risks in your cloud resources, allowing you to make informed decisions, prioritize actions, and strengthen your overall cloud security posture. Explore this widget and take control of your risk management today.
Quick Glance at the Top 4: Revamped Critical Risks widget #
Our revamped Critical Risks Widget brings you actionable insights by showcasing prioritized risks for each selected risk type. Experience a new level of risk awareness as you delve into the most critical vulnerabilities specific to your environment.
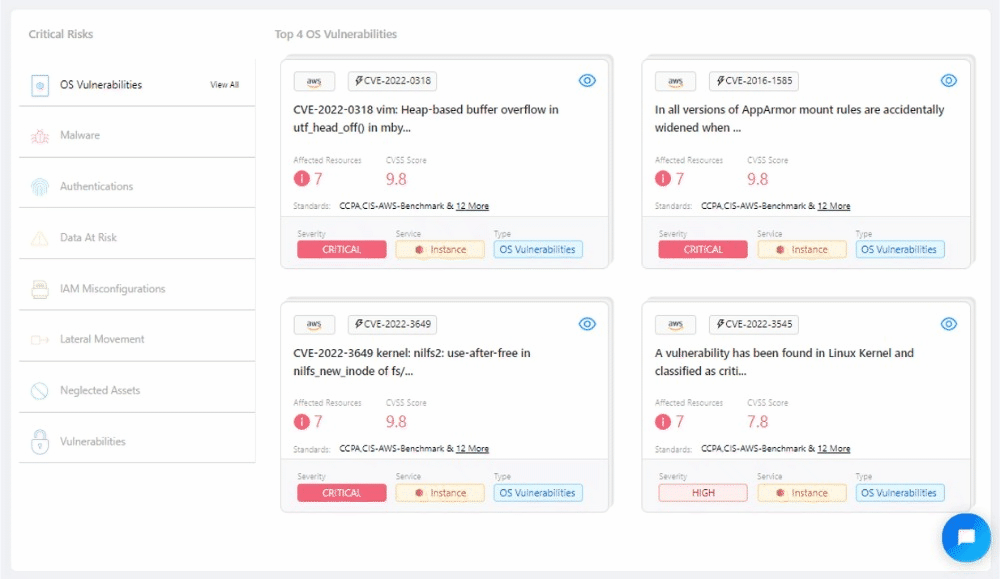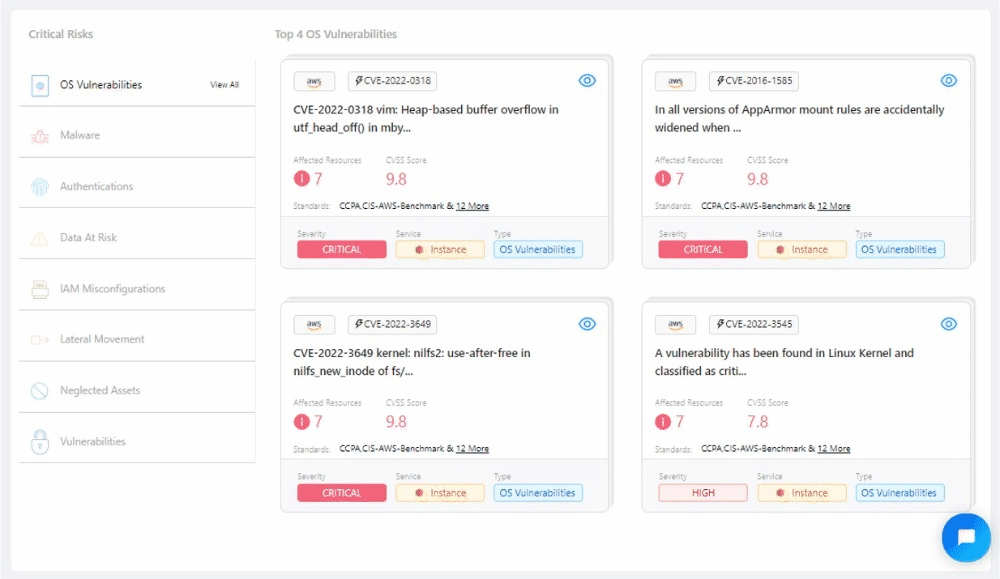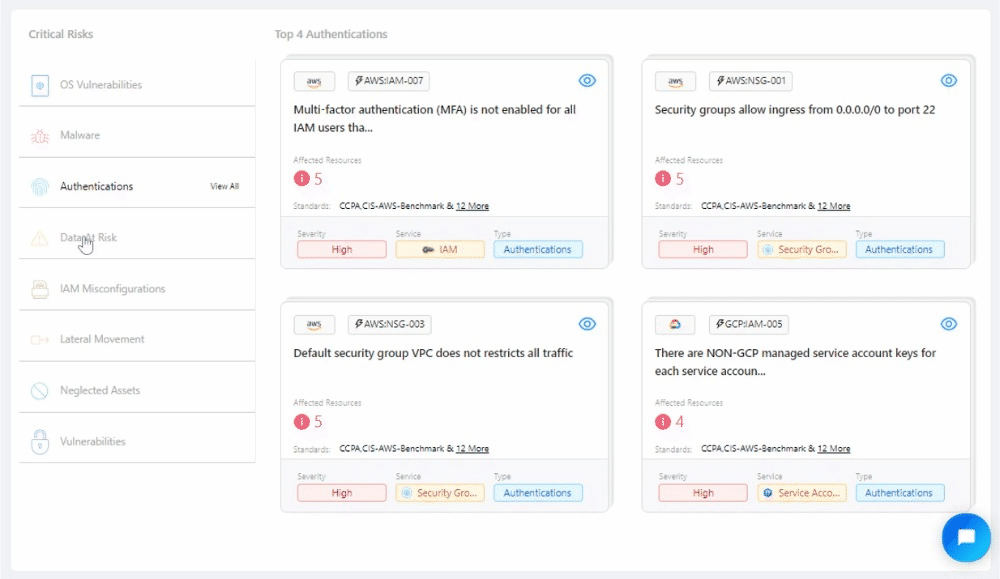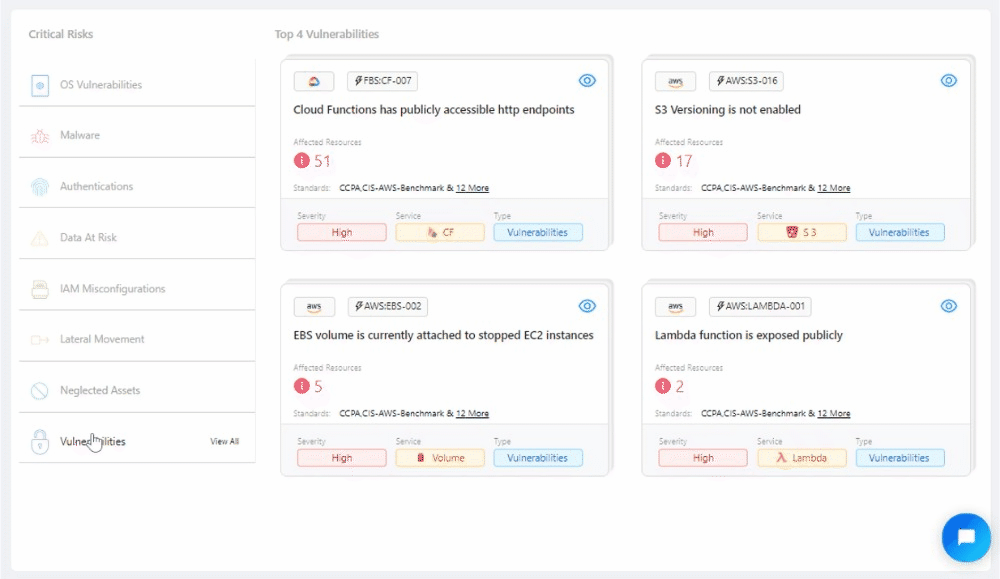
🚀 Other Improvements #
More Powerful Access Control #
The latest enhancements to the Access Control page have been aimed at improving the user invitation process and providing better visibility into invitee responses. These updates empower owners, admins, and DevSecOps teams with a smoother and more efficient user onboarding experience.
1. Streamlined User Invitations #
Previously, the invitation process required users to manually select the “Create User” checkbox when inviting new users to their organization. Based on this selection, the invite was sent or not sent, depending on the existing user status.

With this release, the platform takes charge of determining whether the invitee is an existing user or not, eliminating the need for users to make this decision. The platform now automatically sends the invitation accordingly, simplifying the invitation workflow and reducing the chance of errors.
2. Invitation Status Tracking #
Previously, it was difficult to determine if the invitee had accepted the invitation or even received it.
Now, administrators and owners can confidently track invitee responses from within the platform.

Cloud Account Connection Health #
Previously users had to run a scan every time they wanted to verify if their cloud account was still integrated with Cloudnosys.
But now, with the new Connection Status section on the Edit Cloud Account page, users can conveniently view the connection status of their cloud accounts in a few seconds.

This enhancement empowers you to quickly assess the connectivity and functionality of your cloud accounts and troubleshoot connectivity issues. The test status icons for each component provide valuable insights at a glance.
Cloud Accounts List Glow-Up #

New Columns #
- Last Scanned: Quickly track the recency of scans for each cloud account, enabling informed decision-making based on up-to-date data.
- Protection Level: At-a-glance identification of the protection level (Basic or Advanced) associated with each cloud account for efficient security management.
- Connection Status: Monitor the connection status of each cloud account from 1 page for a quick assessment of integration health.
Combined Columns into One: Account Name #
- Cloud Provider: Name and Provider columns are now combined. Cloud Provider logos appear under the Account Name column, simplifying navigation and improving user experience.
- Account/Project ID: Each cloud account’s Project/Account IDs now appear right below the Cloud Account Name, providing essential identification details for each account.
Re-establish the Connection: Reconnect your AWS Cloud Account #
Say goodbye to connectivity issues and confidently establish a fresh, error-free connection with Cloudnosys while retaining your valuable scan history.

You now have the power to effortlessly reconnect your AWS Cloud Accounts with Cloudnosys. This feature ensures that you can easily re-establish Cloudnosys’ connection to your cloud account without any data loss – maintaining continuity in your cloud security monitoring.
You can find this option on the Edit page of your cloud account.
Flexible Cloud Account States: Active/Inactive #
Previously, managing account access for cloud accounts had limited options.
Now, we have implemented the ability to enable or disable cloud accounts. This means you can now conveniently switch the state of a cloud account between active and inactive based on your specific requirements.
What happens when a Cloud Account gets enabled/disabled?
Enabling a cloud account reactivates its functionality within Cloudnosys, allowing you to resume monitoring, scanning, and managing the associated resources. Conversely, disabling a cloud account temporarily deactivates its integration, ensuring that no further actions or changes are made until re-enabled. This granular control allows you to maintain comprehensive visibility and manage your cloud environment more effectively.

Note:
- The terms “Active” and “Inactive” represent the states of a cloud account, while “Enable” and “Disable” are the actions used to switch between these states.
- Disabling a cloud account is equivalent to marking it as inactive, reflecting its disabled status within Cloudnosys.
Better Sidebar Menu = Better Navigation #
The improved sidebar menu is designed to optimize your navigation experience. With a simplified menu structure and intuitive page hierarchy, effortlessly navigate through different sections and sub-sections of the platform.

Release # 22 – April 3, 2023 (version 2.7.5) #
Description: This release was focused completely on performance optimization and minor improvements.
Affected Components: Security Dashboard Widgets, Risk Drawer, Resource Drawer, Chatbot, Organization Search Bar
⚡ Performance Optimization #
In our continued effort to make Cloudnosys a fast platform, we have optimized its performance in the past few weeks!
Here’s a quick rundown on some of the top optimizations:
Optimized: For some organizations with a high number of resources, the risk drawer was lagging when getting opened.
Optimized: For organizations with a high number of cloud accounts, some combination of cloud accounts was taking an unusually long time to load the widgets.
And many more elements were optimized!
🚀 Minor Improvements #
- The chatbot icon will now be behind the Drawer whenever it gets opened, enabling you to use all the Drawer’s features without any hindrance.
- In the Risk Profile Drawer, the toggle switch of Suppressed Risks toggle has been moved a bit above its last position, giving you more screen space to view the resources below it.
Release # 21 – January 3, 2023 (version 2.7.4) #
Description: This release was focused completely on performance optimization and minor improvements.
Affected Components: Security Dashboard Widgets, Suppression, Resource Drawer, Access Control, Organization Search Bar
⚡ Performance Optimization #
In our continued effort to make Cloudnosys a fast platform, we have optimized its performance in the past few weeks!
Here’s a quick rundown on some of the top optimizations:
Optimized: The creation of suppression rules was not optimized causing other features to take time.
Optimized: Instead of waiting for all the widgets to load at once, the dashboard will begin displaying widgets as they are generated right after a scan.
And many more elements were optimized!
🚀 Minor Improvements #
- If you unknowingly try to invite someone who’s already a part of your organization, Cloudnosys will now let you know it clearly so that you’re not confused when nothing changes.
- Searching from the organization search bar and then switching to another organization will NOT reset the search results anymore. This way, you can switch to another organization again from the same search results without having to search again.
Release # 20 – October 4, 2022 (version 2.7.3) #
Description: This release was focused on performance improvements.
Affected Components: Security Dashboard widgets, Suppression Rules, Signature
🐛 BUG FIXES #
In our continued effort to make Cloudnosys the most reliable security platform, we eliminated a few bugs on the platform in the past few months!
Here’s a quick rundown on some of the top fixes:
Fixed: A signature related to KMS Keys was incorrectly highlighting a risk when it did not exist.
Fixed: A signature related to the IAM password policy was incorrectly highlighting a risk when it did not exist.
Fixed: Status Message was not being displayed for Custom Signatures even after Status Message was provided from the Custom Code.
Fixed: In an extremely rare case, the Security Dashboard widgets showed the widget skeleton only when the widget’s History filter was changed from Current to anything else.
Fixed: Signatures of AMI were showing EC2 instances in the Signature drawer instead of AMI resources
Fixed: The Email Address Verification email had a few typos.
And many more bugs were fixed!
Release # 19 – July 5, 2022 (version 2.7.2) #
Description: This release was focused more on improving your general experience of using the platform along with a few new updates requested by some of our valuable clients.
Affected Components: Scan Engine, Compliance Regulation, Access Module, Alerts, Organization Menu, Cloud Accounts, Account Settings
🚀 NEW FEATURES & IMPROVEMENTS #
FedRAMP Compliance #
We’re delighted to announce that now you can check how compliant your cloud accounts are for FedRAMP (Federal Risk and Authorization Management Program).
FedRAMP is a US government-wide program that enhances a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. This is a key regulation for all North American organizations as well those organizations that work with North American clients.
Just like all other compliance reports, you can easily find the FedRAMP report on the Compliance page.

Cloud Account Permissions for Users #
You no longer need to worry that all the users have access to all the cloud accounts in your organization; because now you can assign permission of specific cloud accounts to users.
Where: Sidebar Menu -> Settings -> Access Control
How: On the Access Control page, under the newly created Cloud Account column, now you’ll be able to assign or unassign one or more cloud accounts to any member of your organization.

Search Bar for Organizations #
You can now search for organizations just by typing in the Organization Search Bar instead of scrolling through the whole list!
Integration of GCP Datastore #
We here at Cloudnosys are all about feedback – especially from YOU! Even though Cloudnosys has the latest GCP Firestore service already integrated, you felt the need for Datastore’s integration and we listened.
Datastore Signatures #
What good is a new service integration on our platform without any signature? Nothing.
Surprisingly, Datastore signatures are actually quite unique – you will not find them with ANY of our competitors! Nonetheless, you can now scan your Datastore for 2 risks through Cloudnosys:
- GCP: DS-001 Ensure that Datastore backup is enabled
- GCP: DS-002 Ensure that GCP Datastore backup is newer than 7 days
Graceful Error Handling of Adding a New Cloud Account #
You will now get to know exactly why your Cloud Account was not able to be added into Cloudnosys when the error is from the Cloud Provider’s end. Previously, it was difficult to identify the issue.
But now, with the help of the error details, it will take you much less time to debug and resolve the issue from your end.
And upon successfully adding the Cloud Account, Cloudnosys will now give you a clearer indication.
As always, Cloudnosys will instantly scan your cloud account for risks as soon as it’s added.
🐛 BUG FIXES #
In our continued effort to make Cloudnosys the most reliable security platform, we eliminated a number of key bugs in the platform in the past few months!
Here’s a quick rundown on some of the top fixes:
Fixed: When the user imports any policy in Custom Policies, rules of only the CCPA policy are imported.
Fixed: Category drop-down menu on Custom Policies page shows duplicates of category names.
Fixed: Outdated Help Center link in Verification Email.
Fixed: GCP Cloud Account service does not appear in Inventory Widgets.
Fixed: The Resources search bar of Playbook Trigger Input settings is showing No Data.
Fixed: Resource Finder stays in the loading state for a bit even after the data is loaded and displayed.
Fixed: Manual Remediation and its Chevron icon are not aligned
Fixed: Incorrect instructions of Step 4 of the modal named “Add a GCP Account to Cloudnosys”.
And many more bugs especially performance improvements as well as scan engine optimization!
Release # 18 – March 10, 2022 (version 2.7.0) #
Description: This release was focused more on improving your general experience of using the platform along with a few new updates requested by some of our valuable clients.
Affected Components: Scan Engine, Compliance Regulation, Access Module, Alerts, Organization Menu, Cloud Accounts, Account Settings
🚀 NEW FEATURES & IMPROVEMENTS #
Integration of more Azure Services #
To provide you with complete visibility of your Azure infrastructure, we have enhanced our footprint by several key services such as
- Azure Databricks
- Azure Disk
- Azure Kubernetes
- Azure Load Balancer
- Azure Service Bus
- Azure Cosmos DB
Improved Experience with Grouped Alerts #
We have added extra functionality in our recently released Grouped Alerts feature to make it more convenient for you:
- The Failed Resources popup of each alert no longer displays the Signature ID for each failed resource. Instead, the Failed Resources popup now displays the name of the service for each failed resource. This means that now you can know the name of the service for every failed resource – right from the alerts.
Previously:
Now: - Clicking on the alert of risk will open the Resource Drawer for you – with details of all the resources failing for that risk.
- The resources will be sorted by Last Seen by default so that you get details of the latest updates on the top.
- The resources identified by the risk alert will be preselected when the Resource Drawer gets opened – making it easier for you to know which resources were part of the alert. This also helps save a considerable amount of time if you want to suppress them altogether instantly.
- If at least one of the resources from the risk alert does not exist anymore in your cloud account, then a fleeting popup will tell you so.
New Azure Signatures #
Our never-ending quest to make your cloud accounts more secure continues!
- AZU: NSG-005 Ensure that the Network Security Group Flow Log retention period is ‘greater than 90 day
- AZU: NSG-006 Ensure that Network Watcher service is enabled within your Azure account subscriptions
- AZU: NSG-007 Ensure that “UDP” Services are restricted from the Internet
- AZU: SA-007 Ensure soft delete is enabled for Azure Storage
- AZU: VM-007 Azure Backup should be enabled for Virtual Machines
- AZU: VM-008 Internet-facing virtual machines should be protected with network security groups
Detection of Network Unavailability #
While using Cloudnosys, have you ever wondered whether your network connection is slow? Or just not working the way you expect it to? Well, you don’t need to go out of your way to verify this anymore!
Now you will get a small pop-up on the bottom right corner of your screen stating whether the platform is facing trouble connecting to the Internet.
Compliance Health Trend Chart in PDFs #
Previously Cloudnosys did not display any visual in the PDF report from the Health Dashboard. But now you will get to see a 2-week summary of the Health of your Cloud Accounts, categorized by Severity.
Minor Improvements #
- Life’s good when it’s easier to differentiate between Cloud Accounts. Previously, we had allowed giving 2 different cloud accounts the same name on the platform. Now you will be alerted when you try to use a name already taken by another cloud account in the same organization.
- The Country/Region field on the Basic Settings (of Account Settings) page is now a dropdown full of names of countries making it easier for you to choose your country instead of typing it.
🐛 BUG FIXES #
In our continued effort to make Cloudnosys the most reliable security platform, we eliminated a number of key bugs in the platform in the past few months!
Here’s a quick rundown on some of the top fixes:
Fixed: No Data on the Billing screen if no cloud account is selected.
Fixed: Rule Expand Icon & Rule Title on the Compliance screen are not aligned on the same line.
Fixed: Role ARN Help modal points are numbered incorrectly.
Fixed: Misspelling of GuardDuty in the tooltip of the Tags field of the Trigger Input section.
Fixed: Double organizations are shown in the Organization drop-down menu when a new one is created.
Fixed: Scan completed popup appears when the user switches to another organization.
Fixed: White space below the horizontal scroll bar in the Playbook Editor.
Fixed: Differences in the Save Risk node’s Input & Output field names.
Fixed: Multiple issues related to the names of organizations in the organization drop-down menu
And many more bugs especially performance improvements as well as scan engine optimization!
Release # 17 – Oct 20, 2021 (version 2.6.2) #
Type: New feature, Feature improvements, and Bug Fixes.
Description: This release was focused on platform stability, Cloudnosys’ API coverage, and a few feature improvements.
Affected Components: Database, UI, Signatures, Reports, Playbooks & Services.
🚀 Feature Improvements #
- API Endpoint to get Widget Reports
Pull dashboard widget reports in JSON format from Cloudnosys via a protected API endpoint, allowing third-party apps to display and utilize Cloudnosys stats. For more details, click here. - Organization Drop-down Menu sorted Alphabetically from A-to-Z
To make it easier & quicker to find an Organization from the Organization Drop-down menu, the list of organization names will appear to be sorted alphabetically from A-to-Z. - Grouped Alerts now display failed resources in Tooltip
The tooltip also contains relevant data about the failed resources such as which cloud account they are associated with. - Unlimited Organizations for Enterprises
If the package is Trial or Paid then the user can add only one organization and if the package is enterprise then the user can add unlimited organizations.🐛 Bug Fixes #
The following minor bugs have been addressed:
- The Billing screen was not showing any data
- Upon clicking “Test connection” another cloud account was being added in some cases
- Access Invite email was not being received for some users
- AWS EagleEye template was not getting downloaded
- The alert for ‘Organization Trial Expired’ had a label of “Invitation” instead of “Trial Expired”
- Full Compliance Report PDF was not getting downloaded when all cloud accounts were selected due to PDF size
- The button “Run till” was running all playbook actions if it was running inside the loop
- A lengthy playbook name was disturbing the User Interface as well as the placement of the buttons
- An auditor had incorrect permissions which allowed them to run a scan, perform a suppression, and run playbooks
- The Organization’s Owner’s Account was not being displayed on the Access Control page
- Playbook Configurable Fields in Settings were not being deleted in some cases
- When Cloudnosys was opened through the Okta app via SSO setup, it was leading the user to the sign-in page instead of the Dashboard
- The “Run Playbook” button was not working in some cases
- Access Control screen was showing an error when sending an invite
- The text of the Past Executions column on the Playbooks screen was not aligned horizontally with the text/icons of the other columns
- After enabling AWS EagleEye, its status looked like it was getting stuck on “Verifying”
- Cloud Account Selector Menu was showing that 1 cloud account was selected even when no cloud account was added to the organization
Release # 16 – Aug 31, 2021 (version 2.6.0) #
Type: Feature & Performance improvements, New Signatures & Playbook Templates, plus Bug Fixes.
Description: This release was focused on implementing numerous Signatures, fixing multiple bugs, and a few minor feature improvements that make Cloudnosys easier to use.
Affected Components: Database, UI, Signatures, Reports, Playbooks & Services.
🚀 Feature Improvements #
- Ticket creation for critical events with details in JIRA Playbook
JIRA Ticket creation of critical events with complete resource details such resource id, cloud account name, region, availability zone along with other important metadata. - User Restrictions on Cloud Account visibility under Organization
User access restrictions on a cloud account level have been introduced in our role-based ARN. This will give organizations the ability to restrict users as per their requirements. So now you can give access to the user(s) to any specific cloud account(s). - Grouped Alerts will also identify resources
The grouped alerts will give users an extended view of all the failed resources detected as a result of the latest scan. - Clickable URLs in System Notifications
All URLs in System Notifications are clickable now – making it quicker and more convenient to go to the relevant URL.
 Signatures #
Signatures #
New Signatures are released continuously and are independent of release dates. Here’s a list of signatures already integrated into the platform since the last release:
Amazon Web Services (AWS) #
- AWS: IAM-023 List of IAM users with Admin access
- AWS: NSG-007 List of Security groups with All TCP/UDP traffic open
- AWS: CW-003 CloudWatch alarms are set up to monitor VPC Internet gateway configuration changes within your AWS account
- AWS: CW-004 CloudWatch alarm must be triggered every time AWS Root Account is used
Google Cloud Platform (GCP) #
- GCP: VM-006 Ensure OS login is enabled for a Project
- GCP-IAM-008 Ensure that Service Account has no Admin privileges.
- GCP-IAM-006 Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at the project level
- GCP: NET-004 Ensure that RDP access is restricted from the Internet
- GCP: NET-003 Ensure that SSH access is restricted from the internet
- GCP: VM-007 Ensure VM disks for critical VMs are encrypted with Customer Supplied Encryption Keys (CSEK)
- GCP: VM-008 Ensure that Compute instances do not have public IP addresses
- GCP: LM-002 Ensure that Cloud Audit Logging is configured properly across all services and all users from a project
- GCP: LM-003 Ensure that sinks are configured for all log entries
- GCP: LM-004 Ensure that retention policies on log buckets are configured using Bucket Lock
- GCP: LM-005 Ensure log metric filter and alerts exist for project ownership assignments/changes
- GCP: LM-006 Ensure that the log metric filter and alerts exist for Audit Configuration changes
- GCP: LM-007 Ensure that the log metric filter and alerts exist for Custom Role changes
Azure #
- AZU: SQLDB-006 Public network access on Azure SQL Database should be disabled
- AZU: SA-004 Ensure that ‘Secure transfer required’ is set to ‘Enabled’
- AZU: SA-005 Ensure that ‘Public access level’ is set to Private for Blob
- AZU: SA-006 Ensure default network access rule for Storage Accounts is set to ‘deny’
- AZU: AD-003 Azure External accounts with owner permissions should be removed from your subscription
- AZU: AD-004 Azure External accounts with read permissions should be removed from your subscription
- AZU: AD-005 Maximum of 3 owners should be designated for your Azure subscription
- AZU: AD-006 More than one owner should be assigned to your Azure subscription
- AZU: KV-004 Diagnostic logs in Key Vault should be enabled
- AZU: VM-006 Insert missing Security & Compliance tags for Azure VMs
 Playbook Templates #
Playbook Templates #
Playbook Templates are actually released continuously and are independent of release dates.
- Remediation: Insert missing Security & compliance Tags for Azure VM Disks

2. Integration: High Priority Alerts of EC2 Alerts to create tickets on JIRA

 Bug Fixes #
Bug Fixes #
The following bugs have been fixed completely:
- For EC2 resources there was an issue with automatic discovery when new resources were created which was identified and fixed.
- Risks notification menu was showing Duplicate Risk Alerts
- Search Filter Bug: In case if the name tag filter of a resource is missing, Cloudnosys will automatically insert the resource ID as the name tag instead of any other tag. This way those resources can be searched and filtered using the resource ID.
- System notification was being shown of another organization.
- The First Seen tooltip of critical resource was showing “N/A”.
- EagleEye template was not being downloaded
- When Suppression Risk was edited from the resource profile, it was creating another Suppression Rule instead of updating it.
- When a playbook was created through remediation, the previous playbook workflow was shown.
- “Create Playbook” was not disabled for users with only view rights.
- Fixed Billing count issue.
Release # 15 – July 15, 2021 (version 2.5.0) #
Type: Feature release, performance improvements, and bug fixes.
Description: Cloudnosys has introduced a new widget for publicly accessible resources and added GCP playbook action along with some important improvements in Playbooks. You can also create automated remediation from the resource profile and signature view. Moreover, new CIS signatures for IAM, Security, Logging, Monitoring & Networking are introduced for recommended security checks.
Affected components: Database, UI, Signatures, Scan, Reports, Filters, Playbooks & Services.
New Features #
1. A new widget added for better visibility of publicly accessible resources

2. Resource Properties are added in the resource profile where you can see some of the metadata associated with a resource.

3. Automated Remediation Now you can create automated workflows to remediate risks as well as resources using Cloudnosys Playbooks feature with just one click!

When you click on “Create Playbook” it’ll directly take you to the Playbooks editor screen with the Cloud Account & Signature details already added by default in the Playbook trigger. This way you don’t have to go to the Playbook separately and type all the relevant details manually in the trigger.
4. GCP Action in Playbooks
This action will share GCP API call capability with the user. Through this node, users can make calls to their GCP infrastructure to fetch resources or make changes on their end (write access required).

5. New Remediation Playbooks added for Azure & GCP
Azure:
- Restrict SSH access on Publicly exposed networks
- Restrict RDP access on Publicly exposed Network
GCP:
- Enable OS login for a VM
- Remove Public IP addresses from Virtual Machine
- Enable Block Project-wide SSH keys for VM

🚀 Improvements #
- Optimized scanning functionality: Now many resources can be scanned within few minutes.
- Added more services in inventory for AWS & Azure:
- AWS Elasticsearch
- AWS Redshift
- AWS Audit – Log
- Azure Log profiles
- New Signatures added for AWS & GCP:
- AWS: IAM-023 List of IAM users with Admin access
- AWS: NSG-007 List of Security groups with All TCP/UDP traffic open
- GCP: VM-006 Ensure OS login is enabled for a Project
- GCP-IAM-008 Ensure that Service Account has no Admin privileges.
- GCP-IAM-006 Ensure that IAM users are not assigned the Service Account User or Service Account Token Creator roles at the project level
- GCP: NET-004 Ensure that RDP access is restricted from the Internet
- GCP: NET-003 Ensure that SSH access is restricted from the internet
- GCP: VM-007 Ensure VM disks for critical VMs are encrypted with Customer Supplied Encryption Keys (CSEK)
- GCP: VM-008 Ensure that Compute instances do not have public IP addresses
- GCP: LM-002 Ensure that Cloud Audit Logging is configured properly across all services and all users from a project
- GCP: LM-003 Ensure that sinks are configured for all log entries
- GCP: LM-004 Ensure that retention policies on log buckets are configured using Bucket Lock
- GCP: LM-005 Ensure log metric filter and alerts exist for project ownership assignments/changes
- GCP: LM-006 Ensure that the log metric filter and alerts exist for Audit Configuration changes
- GCP: LM-007 Ensure that the log metric filter and alerts exist for Custom Role changes
4. GCP Cloud account improvements:
- Users will be notified via email & system notification if there are any errors in connection.
- While adding a cloud account if a user skips any mandatory permissions, or if they forget to enable any relevant APIs, the user will be notified via system notifications.
5. Alerts Optimization
- Risks alert group by signatures in the notification
- Email alerts will be sent for every Cloud Account now instead of Organizations
- Notification Alerts will now be shown with respect to the organization
Minor Improvements
- Scan progress bar changes.
- Improved “Scan failed” error messages.
- Improvements in Playbooks action “Custom code”.
- Improved service filters for EC2.
- The playbook execution history is now real-time. It will be updated automatically.
Bug Fixes #
- Fixed history issue in Playbooks.
- Fixed time format issue in health trends.
- Fixed suppression menu issue.
- Fixed scan monitoring issue.
- Fixed total resource count at billing screen.
- Fixed error messages for cloud accounts.
- Compatibility issues with AWS findings were resolved.
Release # 14 – February 19, 2021 (version 2.1.0) #
Type: Feature release, performance improvements, and bug fixes
Description: Cloudnosys introduces new actions for Playbooks with better UI, signatures for AWS EKS, AWS Config, AWS API Gateway & AWS ECR. This release introduces pre-made Playbook templates for integrations and remediations. This release also includes bug fixes and improved performance.
Affected components: Database, UI, Signatures, Scan, Reports, Filters, Playbooks, Services
New features added as follows: #
1. New Triggers for Playbook #
- Schedule Trigger:
In scheduled trigger, you need to set time interval (hourly/weekly/monthly) and the playbook is triggered according to it
- Manual Trigger:
In manual trigger, the playbook is run when you click on the “Run Playbook” button.
2. New Actions for Playbook #
- Custom Code:
Through this action, you can write custom logic & use JavaScript functions
- HTTP:
HTTP action can fetch data from third-party endpoints and make API requests through URL
- Loop:
In the loop, you can add multiple actions & they will iterate based on the conditions defined
- Get Resources:
This action can get resources that are already scanned in the Cloudnosys platform.
- Save Risk:
Save risk action can save risks from any data source in the Cloudnosys platform.
3. Playbooks Template feature #
You can create a Playbook by using a list of templates, you just need to click on “Add playbook” and then click on “Browse templates” and then you’ll see a list of available templates.
By clicking on “Use Template” you can use that template and modify it according to your preference. There are some global values that you need to add, so when you pick a template you’ll see a modal for global referencing:
By adding them, you don’t need to add input values instead you can reference input fields (e.g Cloud Account, Service) in your playbook actions for instance you want to reference cloud account then write “${global.cloudAccount}” in cloud account input field
4. New templates for integration and remediation #
Now you can create a playbook by using templates. Templates added for:
Remediation:
i) S3 Bucket Remediation
ii) AWS Security group Remediation
Third-party risk integration:
iii) AWS Inspector and Kube-bench findings
iv) AWS container security
5. New Signatures added #
Following new signatures added for AWS Glue, AWS API Gateway, AWS EKS, and AWS ECR
- AWS:GLUE-001: This signature prevents unauthorized users from getting access to the logging data in AWS CloudWatch if encryption at rest is enabled for your Amazon Glue security configurations.
- AWS:GLUE-002: This signature ensures that at-rest encryption is enabled when writing AWS Glue data to Amazon S3.
- AWS:API-001: This signature checks if active tracing is enabled for your Amazon API Gateway API stages to sample incoming requests and send traces to AWS X-Ray.
- AWS:API-002: This signature ensures if AWS Web Application Firewall (WAF) is integrated with Amazon API Gateway.
- AWS:API-003: This signature ensures that AWS CloudWatch logs are enabled for all your APIs created with Amazon API Gateway
- AWS:ECR-002: This signature checks that if your AWS Elastic Container Registry (ECR) repositories are configured to allow access only to trusted AWS accounts.
- AWS: EKS-002 This signature checks if your Amazon Elastic Kubernetes Service (EKS) clusters have control plane logs enabled.
- AWS: EKS-003 This signature ensures if your Amazon Elastic Kubernetes Service (EKS) clusters are using the latest stable version of the Kubernetes container orchestration system.
- AWS:EKS-004: This signature checks that if your Amazon EKS cluster’s Kubernetes API server endpoint is not publicly accessible from the Internet.
- AWS: CONFIG-001 This signature verifies if AWS Config is enabled in all regions.
- AWS: CONFIG-002 This signature checks if the Amazon Config service is referencing an active S3 bucket.
6. UI Changes #
The Time interval for Eagle eye alerts
- Time Interval for generating Eagle eye risks. So now you can set time intervals for alerts & then you’ll receive eagle eye alerts accordingly
Ability to deactivate Eagle-Eye (Real-time monitoring)
- Permanently/Temporarily disable eagle eye:
When you click on disable Eagle eye you’ll get a message “Do you want to disable Eagle eye” with two options “Temporarily disable” and “Permanently disable” If you select “Temporarily disable” you’ll not receive Eagle eye alerts and Eagle eye will be disabled temporarily.
You can simply enable it by turning the switch button ON.
And if you select “Permanently disable” then Eagle eye will be disabled permanently but you have to delete the stack set from your AWS account. Note: If you want to enable Eagle eye then you need to perform all steps for the Eagle eye setup.
7. Eagle-Eye Improvements #
Now Eagle can provide real-time alerts for AWS S3 and AWS EC2 in addition to previous services. So whenever any change in the console is made for instance S3 bucket versioning is disabled then you’ll receive an alert for that.
Other Improvements: #
- Added new services in inventory for AWS, Azure, and GCP
- Updated descriptions for some playbook actions
Bug Fixes #
- Some service names were inconsistent
- The suppression menu was overlapping vertical scroll
- Description for some signatures was outdated
- The loader was shown behind the execution modal of the playbook
- Fixed trial message line break issue at Billing screen
- Corrected some spelling issues in the signature description
- Playbook update time was syncing with execution time
- Fixed permission issues regarding some user roles
- Playbook history issue fixed
- Service name consistency for AWS, Azure & GCP
Release # 13 – November 27, 2020 #
Type: This release improves performance & fixes bugs
Affected components: Database, UI, Signatures, Scan, Reports, Filters
Improvements:
- Risks Scan Performance improved by 2x
- New Cloud Services added: Amazon Elastic Container Service (Amazon ECS), Amazon Elastic Kubernetes Service(Amazon EKS), and Amazon Elastic Container Registry (Amazon ECR)
- Following New, Signatures added for AWS ECS, AWS ECR, and AWS EKS
— AWS: ECS-001: This signature checks if your Amazon Elastic Container Service (ECS) clusters have the CloudWatch Container Insights feature enabled.
— AWS: ECR-001:This signature identifies if there are any exposed Amazon ECR image repositories available within your AWS account.
— AWS: EKS-001: This signature checks if the security groups associated with your Amazon Elastic Kubernetes Service (EKS) clusters are configured to allow inbound traffic only on TCP port 443 - Custom signatures add to Custom Regulations
- Updated GDPR regulation
- Improvements to the user onboarding experience
- Improvements in Alerts suppression to accept more complex suppression rules
Bug Fixes
- Services filters didn’t display correctly
- Report PDF couldn’t be downloaded for some customers
- Multi-Organization/Tenant did not auto-create with correct users
- Cloud Accounts were not being added in some regions
- Signature descriptions/labels were outdated
Release # 12 – October 27, 2020 #
Type: This release adds new features, fixes bugs & improves performance
Description:
Cloudnosys introduces new screens for regulations & cloud accounts with better UI & performance. Also, new user roles were added to manage access control.
Affected components: Database, UI, Signatures, Scan, Reports, Filters
Improvements:
Features updated as follows:
i) New screen for Cloud account
- The onboarding process improved by adding new policies and step by step guide for adding IAM role
ii) Added more roles in access control such as Administrator & DevSecOps for better management of role-based access
iii) New screen for regulations
- Added rules, which makes it easier to keep a track of risks that are available in each rule
- Risks tab added, which allows users to check how many risks are present in a particular regulation
iv) Others:
- Changes in API Engine for AWS
- Scan progress bar UI updated
Bug Fixes
- Scan fixes
- Fixed alignment issues at regulation screen
Release # 11 – September 08, 2020 #
Type: This release adds better performance & fixes bugs.
Affected components: Database, UI, Scan, Reports.
Improvements:
1. Improvements in scan performance
2. Added Detailed Execution history for Playbooks
3. Improved UI for change password screens
4. More types of notifications added on Access Control2. Bug Fixes
5. Fixed a UI glitch with filters on Signature Views
6. Fixed display of historical data on trends widgets
7. Fixed minor issues on Custom regulation reports
Release # 10 – August 10, 2020 #
Type: This release adds better performance & fixes bugs.
Improvements:
1. Reports & Widgets now load faster. Reports and Widgets now load 5x faster when the scan is completed.
2. New security checks by the Cloudnosys team can now be added faster. We’ve added a new module that helps our development team in adding new Security postures quickly, so they can be available for our customers at the earliest.
3. New Security checks for Azure.
Private Links
4. Moved email address settings into Account Settings > Security Settings
Now emails can only be updated based on inputting your current password for better security reach.
UI/UX improvements
5. Fixed text dropping issues on the signature status tooltip.
6. Updated labels for the suppression settings screen.
7. Table cut issues for some specific screen resolutions.
Release # 09 – July 23, 2020: #
Type: This release adds new features, fixes bugs & improves performance
Features
1. Google Cloud Platform Cloud Account
Cloudnosys has now the capability to scan GCP resources on its platform. Users can now check their inventory, security postures, compliances, and add governance to their GCP infrastructure via Cloudnosys.
2. GCP added in Custom Signatures
Users can now create their custom signatures via our code editor using a wide variety of resource types already included in our system.
3. GCP added in our Custom Regulation
Users can now create custom policies using our custom regulation tools for their GCP infrastructure. It supports all our pre-built signatures and also custom signatures if a user has created any.
4. Better inventory collection for GCP
Cloudnosys use GCPs Asset API to scan resources from a user’s infrastructure and also cover their Firebase assets. This helps us cover a great scope of resources for the user so we could provide better inventory coverage.
5. Added CCPA Regulation
Improvements
1. Most critical resources are now shown on a single page instead of paginated.
2. Icons changed for inventory widgets.
3. Better shades for priority notifications of high, medium & low.
4. Adjusted spacing for better readable content.
Bugs
1. Fixed UI and spacing issues for widgets.
2. Fixed explorer spacing issues to adjust content.
Release # 08 – July 03, 2020: #
Type: This release adds new features, fixes bugs & improves performance
Features
1. Playbooks
Playbooks give the user the ability to automatically remediate and orchestrate an immediate response on specific actions. Playbooks can also help achieve automatic remediation on Risks that Cloudnosys detects and generate emails to inform the concerned person/department.
2. More Resource coverage in services
We’ve broken our EC2 service into Instances, Volumes, Security groups, and Elastic IPs. So users can now deep dive into their EC2 inventory and have more coverage of their resource health.
3. Billing Dashboard
Users can now view their billable resource counts and get a sense of an idea on how much they’re being billed by Cloudnosys. The billing dashboard only counts resources that are currently active on your cloud infrastructure.
Improvements
1. Improved Scan Engine performance.
2. Improved dashboard widget performance.
3. Added filters for new resources that come under specific service umbrellas such as EC2.
4. Added more services & security checks for AWS & Azure
For AWS:
— Key Management Services
— Dynamo Database
— Elastic Load Balancers
— Cloud Watch Alarms
— Cloud Watch Events
For Azure:
— Added security checks for Web Apps
Bugs
1. Fixed count issues between Widgets and Explorer.
2. Fixed resource status issues when viewed from the Signature drawer.
3. Fixed UI issues.
Release # 07 – June 11, 2020: #
Type: This release adds new features, fixes bugs & improves performance
Features
1. View Historical data on Widgets
Now Users can view historical data on their widgets on Security & Compliance dashboards, giving them more power and analytics to compare their data with previous dates.
2. View historical data on Explorer
Now users can also track back their data on the Explorer (Sidebar) which can be popped by clicking on widgets from the Compliance and Security dashboard. Users can select previous data from the latest previous date.
3. View 7 & 30 days trends
We’ve improved our trends data to now include 7 & 30 days older data. Users can have a more analytical approach to how their risks are changing with time.
4. Added NYCRR Regulation
Improvements
1. Most critical risks now show counts of only failed signatures in a resource on the widget.
Bugs
1. Fixed map locations on Risks by Region widget.
2. Fixed VPC collection methodology to include better network-related resources.
Release # 06 – May 13, 2020: #
Type: Feature release and performance improvements
Description: Cloudnosys introduces new widgets for security posture with better UI & performance, resource enhancements, and the introduction of a new dashboard called “Health dashboard”. New signatures for Lambda, IAM, VM & some others are added.
Affected components: Database, UI, Signatures, Scan, Reports, Filters
Features updated as follows:
1. New Widgets for Security Dashboard
- Security Posture
- Inventory
- Critical Risks
- Most critical Resources
2. New Widgets for Compliance Dashboard
- Compliance Overview
- Security Groups
- Regulations
- Compliance Standards
3. Health Dashboards
- Risks by Severity
- Risks by Cloud Account
- Risks by Category
4. New Signatures added for Lambda
5. UI Changes
- Added time icon in widgets
- Risks by Region stats shown with a bar chart
- In compliance dashboard, compliant bar added in Compliance Standards which will show users how much the resource is compliant
New items added:
- Risks by Region widget now show heat maps on regions that have risks categorized in severity circles (red-high,yellow-medium,blue-low). Upon hovering, users can see their total risks & region
- Added 3 new lambda signatures.
- Improved explorer performance
- Widgets count will show only unsuppressed resources
- Resources Explorer now loads instantly.
- PDF reports are now cached for faster display and generation. This helps users instantly download copies of them without any processing or wait time.
Release # 05 – March 11, 2020: #
Features
- Custom Signature
Create your own Custom signatures through our premium feature of Custom Signatures that comes along with a code editor with complete code IntelliSense. - Explorer
A dynamic sidebar that displays all your resources and their statuses. You can drill down using different filters like region, categories, or even which of them are compliant or not. - Playbooks
Playbooks are our automatic security orchestration tool. That helps you take immediate actions based on any event occurring on your infrastructure through our platform. - Suppression
Users can suppress alerts/notifications that are not relevant to their scope, by doing so, its absence does not affect the normal presence of the resources. The suppression option occurs on the Resources tab or on any specific risk that a user wants to hide. - Access Control
AC (Access Control) provides users to create their separate organizations, add users to their organizations and create new users that only reflect on their organization.
Features Updated
- Cloudnosys has updated the Scanning mechanism. Now Scanning for resources takes 30 to 40 seconds to complete.
- Cloudnosys has improved the PDF download and it can be downloaded into two formats now. (e.g. Executive Summary & Full Report)
- Cloudnosys added more app integrations (SAML, Okta, OneLogin, ServiceNow).
- Cloudnosys has updated additional signatures of AWS and Azure.
- Cloudnosys now provides a MultiAccount Selector, that can be used to run scans on multiple accounts at the same time.
Bug Fixes
- This release resolves the Signature layout issue on Edge and Firefox.
- This release resolves the issue of multiple ‘Scan already in progress’ pop-ups. Now a single pop-up displays multiple cloud accounts’ scan progress.
- This release updates email settings that are now replaced from basic to security settings.
- This release resolves the issue of delay in the ‘Create User’ email, which is now sent instantly to the user.
Release # 04 – August 2, 2019: #
Features
- App Integration
Cloudnosys provides the facility to get delivery of alerts on your custom apps (Slack, Webhook) in a matter of minutes and without a single line of code. Now, you can Integrate your custom apps to Cloudnosys and get notified of the security risks and alerts in your cloud infrastructure so your team is always up to date with security and compliance posture. - Custom Regulation
Cloudnosys allows users to create new policies or customize provided regulations for your infrastructure with distinguished custom rule sets that can generate reports on specific resources. - Azure Signatures
Cloudnosys has added around 10 new control sets for Azure.
Features Updated
- Cloudnosys has updated the signature catalog filter with Azure Categories. You’re now able to view the filtered view of Azure control sets.
- Cloudnosys has updated the User facing documentation with details of the new feature, Integration.
Bug Fixes
- This release resolves an issue with the Alerts UI.
- This release resolves issues with Forget Password Link.
- This release resolves the compliance report bugs.
- This release resolves the issue with CloudEye Alerts.
Release # 03 – June 20, 2019: #
Features
- SOC-2 Services Organization Control
Cloudnosys has added a new report that is built using the American Institute of CPA (AICPA.org) SOC 2 Controls (2017). AICPA guide on Reporting on Controls as noted as Service Organization Relevant to Security, Availability, Processing Integrity, Confidentiality, or Privacy specifies the components of a SOC 2. - GDPR (EU) 2016/679
Cloudnosys has added The General Data Protection Regulation (EU) 2016/679. It
is a legal framework that sets guidelines for the data protection, collection, and processing of personal information of individuals within the European Union (EU). Superseding the Data Protection Directive 95/46/EC, the regulation contains provisions and requirements pertaining to the processing of personal data of individuals (formally called data subjects in the GDPR) —regardless of its location and the data subjects’ citizenship—that is processing the personal information of data subjects inside the EEA. - Cloudnosys Custom Compliance Report
Added Cloudnosys Custom Compliance Report developed by our experts to evaluate different security parameters such as Audit Log, cryptography, Access Logging, Data Protection, etc. - Account Center
Added billing section in the Cloudnosys environment having details about the licensable resources in the user’s account and their instances. - Admin Panel
Users with Administrator access to manage and control cloud accounts. An admin view screen containing a list of all accounts and allowing Admins to edit or update a user profile, user package, and expiry date from the panel. - Region Selector
Added a region selection step to the Add Account process. Now you must choose a region to create a cloud account. - Full-Protection Policy
Added AWS Full-Protection Policy that vigorously governs the security aspects and imposes best practices. This policy quickly mitigates cloud vulnerabilities and misconfiguration and allows one-click remediation. - Azure Signatures
Added 15 new control sets for Azure.
Features Updated
- Cloudnosys has Improved the dashboard usability by adding a scan date selector. You’re now able to view compliance reports of a particular scan date selected from the selector.
- Cloudnosys has improved the Edit cloud account option by allowing users to change their selected policy.
- Cloudnosys now includes compliance reports after scan completion in email notifications. The compliance report now consists of Risks (failed signatures), Passed signatures, and Compliance status.
Bug Fixes
- This release resolves an issue with the Remediation button on the correlation policy. The Remediation button now displays and works as expected.
- This release resolves an issue with downloading PDF reports in the Cloudnosys dashboard.
- This release updates an error message that appears when a read-only user tries to access remediation.
- This release resolves an issue related to the Risk Alerts emerging after enabling EagleEye.
Release # 02 – December 2, 2018: #
Features
- CIS AWS Benchmark Version 1.0
Cloudnosys updated the CIS AWS Foundations Benchmark report in the Cloudnosys console of version (1.0) of the CIS AWS Foundations Benchmark. Users can now assess their AWS accounts against the latest CIS AWS Foundations Benchmark guidelines, including multi-factor authentications, AWS Config auditing, review of VPC peering network rules, review of IAM policies, access key rotation, and other improvements. For more information about the CIS AWS Foundations Benchmark report, see CIS Benchmarks. - PCI Data Security Standard (PCI DSS 3.2)
Cloudnosys added a new report, the PCI DSS report that covers technical and operational practices for system components included in or connected to environments with cardholder data. - NIST 800-53 Rev 4 – FedRAMP / High
Cloudnosys has added a new report, NIST 800-53 Rev4 that is a publication that recommends security controls for federal information systems and organizations and documents security controls for all federal information systems, except those designed for national security. - Alerts UI
Cloudnosys introduces an Alerts section that pushes notifications of risks and threats in the user’s Dashboard. - Health Dashboard
Cloudnosys added the Health dashboard which consists of graphs on the summary of your cloud environment with detailed health statistics about Risks with respect to Groups and Scans. - PDF Report
Added ‘Export PDF’ button that facilitates users to download their complete compliance report with all Risk summaries and Signature level details in PDF format for record-keeping. - Monitoring/Scheduling
Cloudnosys provide more control to your scan schedules by automating the span of vulnerability scanning. It allows scheduled scanning with daily, weekly, and monthly intervals. - EagleEye
Cloudnosys provides Real-Time Threat Detection System that monitors your Cloud infrastructure and detects risks with continuous alert notification to the User’s Cloudnosys Dashboard. - User Account Verification
Instant email notification on user-specified email to verify the new registration on Cloudnosys. - Scan Progress Bar
Cloudnosys has added a progress bar showing the progress of cloud account scanning with scan percentage and time of completion.
Features Updated
- Cloudnosys has Improved the AWS Audit policy that now actively manages the security groups and grants users to audit and monitor security trails.
- Cloudnosys has upgraded its usability with the addition of an Edit profile facility allowing users to edit their account info and reset passwords.
- Cloudnosys has now expedited the Scan Capability which now completes the scan and updates the whole dashboard within a min.
Bug Fixes
- This release resolves an issue with the Total Risk Count on the Compliance dashboard. All counts are now accurate.
- This release resolves an issue with filters on the signature catalog page. All filters appear as intended now.
- This release resolves a cosmetic issue with the layout of the View Resource drawer.
- This release resolves an issue related to the no. of resources and status of signature IAM-007.
- This release resolves an issue related to the scan duration of cloud accounts.
Release # 01 – July 16, 2018: #
Features
- ISO/IEC 27001
Cloudnosys has added ISO 27001/27002 report which is a widely-adopted global security standard that sets requirements and best practices for a systematic approach to managing company and customer information that is based on periodic risk assessments appropriate to ever-changing threat scenarios. - HIPAA Regulatory Citation
Cloudnosys has added The Health Insurance Portability and Accountability Act of 1996 (HIPAA), sets the standard for sensitive patient data protection. Companies that deal with Protected Health Information (PHI) must have physical, network, and process security measures in place and follow them to ensure HIPAA Compliance - Signature Catalogue
A comprehensive list of signatures is used across the dashboard with easily operated filters. - AWS Signatures
Added 25 new signatures for AWS across multiple compliances. - Compliance Dashboard
A comprehensive view of risks in the dashboard with respect to functions along with Total Risks all over the dashboard. An additional field that allows users to select the cloud account they want to see the statistics of.
Bug Fixes
- This release resolves an issue where metadata was missing on some log sources.