
What to Consider When Choosing a Cloud Security Provider
Why Cloud Security Providers Matter in 2025 Imagine your business’s data as a vault. Without a skilled guard, even the strongest lock can be picked.


Why Cloud Security Providers Matter in 2025 Imagine your business’s data as a vault. Without a skilled guard, even the strongest lock can be picked.

In today’s digital world, protecting sensitive data requires careful attention, especially in a cloud setting. Role-Based Access Control or RBAC is one of the powerful

Why Cloud Security Governance Isn’t Just Another Buzzword Imagine your cloud environment as a bustling city. Without traffic lights, speed limits, or law enforcement, chaos

Welcome to the Essential Guide to Cloud Security for Remote Work (2025). Remote work is no longer a temporary shift; it’s a fundamental change in

What is DeepSeek AI? DeepSeek AI is an advanced artificial intelligence technology that has been making waves in the tech industry. It uses complex algorithms

Cloudnosys · AI and ML in Cloud Security As cloud adoption grows, so do organizations’ security challenges in protecting their data and infrastructure. Traditional security

As organizations embrace cloud technology, maintaining security in this environment is essential. A well-defined cloud security policy provides a framework to protect data, comply with

In today’s swiftly evolving digital panorama, corporations of all sizes increasingly embrace cloud technologies to pressure increase, decorate collaboration, and optimize operations. However, the shift

As more organizations migrate their operations to the cloud, the need for robust and streamlined security solutions is greater than ever. Traditional security management approaches

Cloudnosys · How Cloud Security Platforms Boost Operational Efficiency In today’s digital age, businesses of all sizes rely heavily on cloud computing. With this reliance
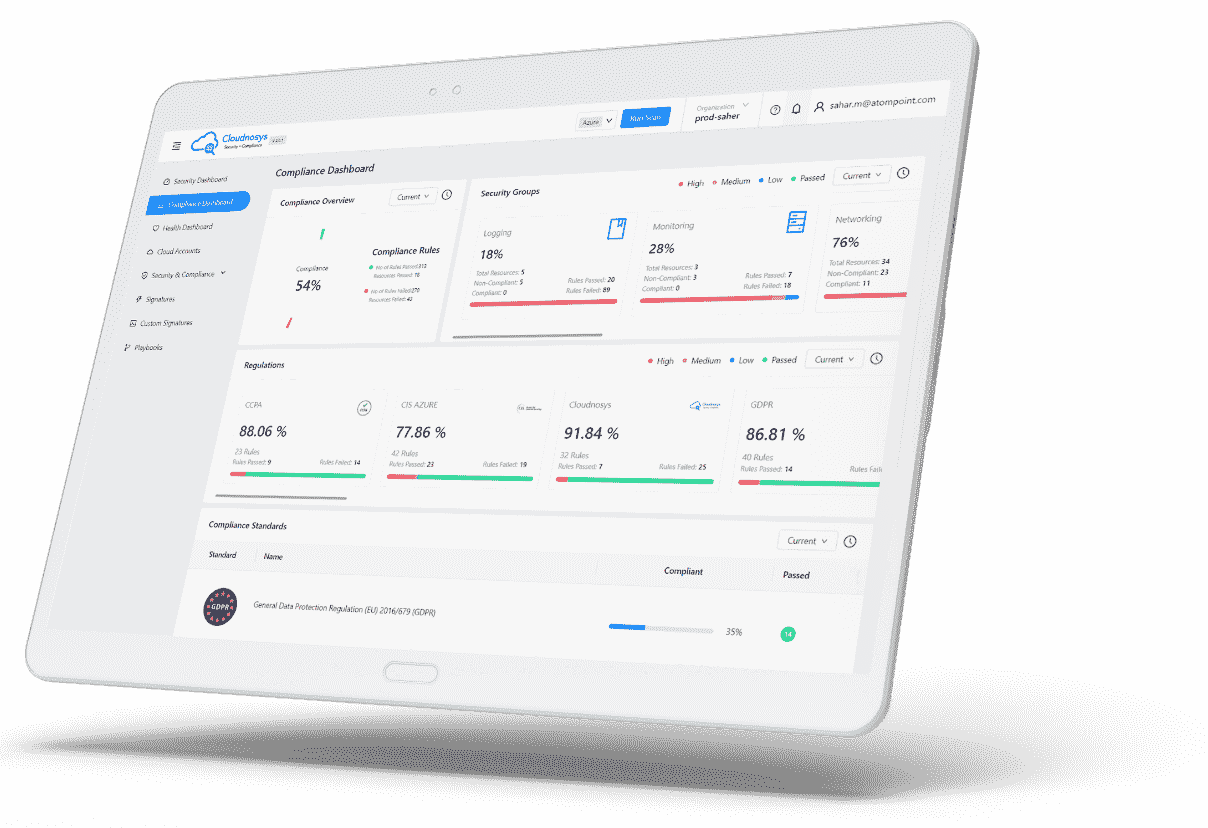
Stay updated with all that you really want to get aware of in cloud security and our most recent researches.