Security Trends That Would Shape the Year 2022
Working remotely during the pandemic has triggered some organizations for cloud migration, which needed to move to the cloud practically for the time being to


Working remotely during the pandemic has triggered some organizations for cloud migration, which needed to move to the cloud practically for the time being to

Cyber security, especially ransomware, has been a big challenge across the globe. Gartner predicts that 75% of CEOs will be personally liable for cyber-physical security

Customers are used to being able to use a lot of internet tools within their environment. They have a lot of security controls. We have

Often we think about the tactical implementation of cybersecurity controls as “security” without thinking about the overarching objective. Insufficient integrations of security tools, triage, and

It is most certainly important to know your cloud environment when it comes to SaaS solutions. Most CIOs & security professionals are not fully aware

Technology is very important and enhancements are happening every day but technology can never solve the entire problem. Companies get hacked and compromised all the

Cloud security solutions and many shield workloads and resources running on public cloud services which solve many challenges, however, how do you select them for

“Flying by the seat of the pants must have been a great experience for the magnificent men in the flying machines of days gone by,

“The number of connected devices means potential vulnerabilities and insecure end-points are growing exponentially”- Johan Paulsson, CTO, Axis Communications With the growing inclination of organizations

“The complexities of cloud computing, and the chance of human error will bite you, so don’t skimp on security planning before deployment or security validation
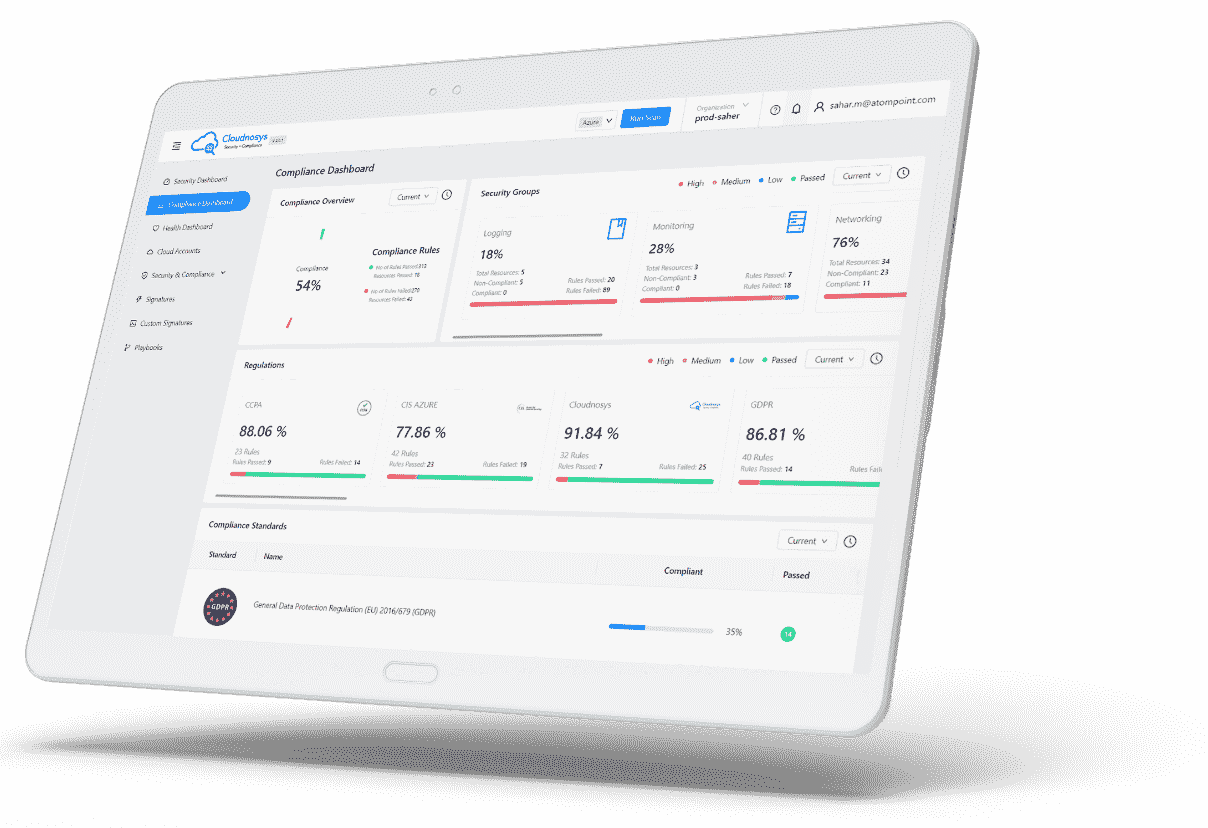
Stay updated with all that you really want to get aware of in cloud security and our most recent researches.