Moving your company to the cloud for gaining speed, flexibility, and better customer experience is a smart digital move. In this regard, your developers are innovating with the agility that demands to spin cutting-edge machines promptly, adding resources, changing configurations and providing more access to cloud resources to enhance collaboration. All these dynamic changes introduces complexity in Cloud Compliance | Security Analytics and expense risk to your business. There is no uncertainty in the fact that managing these with no automation is a real challenge. Nowadays, the increasing utilization of multiple disjointed tools for managing complexity from maintaining compliance to monitor security controls, resolve issues and manage cloud operations results in elevating your business budget and lead it to a downturn. Therefore, it’s high time to bring together Cloud Compliance | Security Analytics to achieve greater security posture.
How To Maintain Cloud Compliance | Security Analytics?
The main reason why most organizations hang back to engage completely in a cloud-first strategy is security and compliance. Most business executives are hard-pressed about how they can have access to a system of intelligence that can put an eye on their cloud services. Besides, they must be able to not only secure them but keep it compliant also for all the compliance regulations. However, an in-depth understanding of how compliance is achieved in the public cloud empowers the organization to finance the growth and agility of the business that is provided by the public cloud. Subsequently, heterogeneous companies can function in this ever-changing regulatory environment. Let’s take a deep dive into the top-quality Cloud Compliance | Security Analytics best practices looks like: Top 10 things you can execute on now to help you protect your data and applications. These are strategies that requires lots of manual efforts but you can get there slowly but surely. Another way to fastrack via Automation would be to leverage Cloudnosys EagleEye platform.

01- AWS CloudTrail
The service that enables compliance, governance, risk and operational auditing of your AWS account are known as AWS CloudTrail. With this service, you cannot only log but can keep your account activity across your AWS infrastructure along with continuous monitoring as well. It provides command-line tools, AWS SDKs and the event history of your account activity which includes actions of AWS Management console. This history simplifies resource change tracking, security analysis, and troubleshooting. Moreover, it detects all sorts of unusual activity occurs in your AWS accounts. They assist in simplifying troubleshooting and operational analysis. This generates lot of data and need post processing with custom scripts. Cloudnosys has a way to analyze your trail and lift off high risk events and tie that to compliance.
How can you leverage with AWS CloudTrial?
- Simplified Compliance
AWS CloudTrial helps you in simplifying your compliance audits via automatic storing and recording event logs for those actions made in your AWS account. Integration with AWS CloudWatch Logs is a convenient way to look for log data, accelerate incident investigations, identify out-of-compliance events and expedite responses to auditor requests.
- Analyzing signals in Trials
You can find and troubleshoot operational and Cloud Compliance | Security Analytics issues through capturing a complete history of changes that takes place in your AWS account within a particular time. This requires building scrips to lift signals and map to compliance standards.
- Visibility Into Resource and User Activity
Get visibility into your resource and user activity by recording API calls and actions of the AWS Management Console. In this way, you can easily identify which accounts and users are called AWS, the source IP address for making calls and when they occur.
- Security Automation
The AWS CloudTrial allows you to track and respond to those account activities that threaten your AWS resources security. Integrating Amazon CloudWatch Events allows you to define workflows that perform when events are detected which may result in Cloud Compliance | Security Analytics vulnerabilities. For instance, when CloudTrail records an API call for making the bucket public, you can build a workflow to apply a specific policy to an Amazon S3 bucket.

02 – IAM
Identify and access management is an AWS service that supplies access control and provisioning proficiencies for AWS users. The administrators of AWS utilize IAM for creating and managing AWS groups and users. They employ granular permission regulations to users and groups for limiting access to AWS resources and APIs. The organizations can make the most of IAM by performing the following:
- While generating IAM strategies, make sure that they are attached to roles or groups instead of individual users. It minimizes the danger of an individual user who is acquiring excessive and extra privileges or permissions by accident.
- The provision approach to a resource by using IAM roles as compared to delivering a credentials’ individual set for access ensures that compromised or misplaced credentials are not leading to unauthentic access to the resource.
- Be certain that the IAM users are provided minimum access privileges to the resources of AWS that permit them to fulfill their job obligations.
- Being the last defense line against a compromised account, make sure that all the users of IAM have activated multifactor authorization for their personal accounts, and restrict the users of IAM with administrative privileges.
- Rotate IAM access keys every day and systemized on a chosen number of days to the expiration of password for ensuring that data is not able to access the potential stolen or lost key.
- Apply a robust password strategy that requires least 14 characters with one upper case letter, one number, and symbol. Enforce a policy of password reset that safeguards users to use a password they have used in their previous 24 password resets.
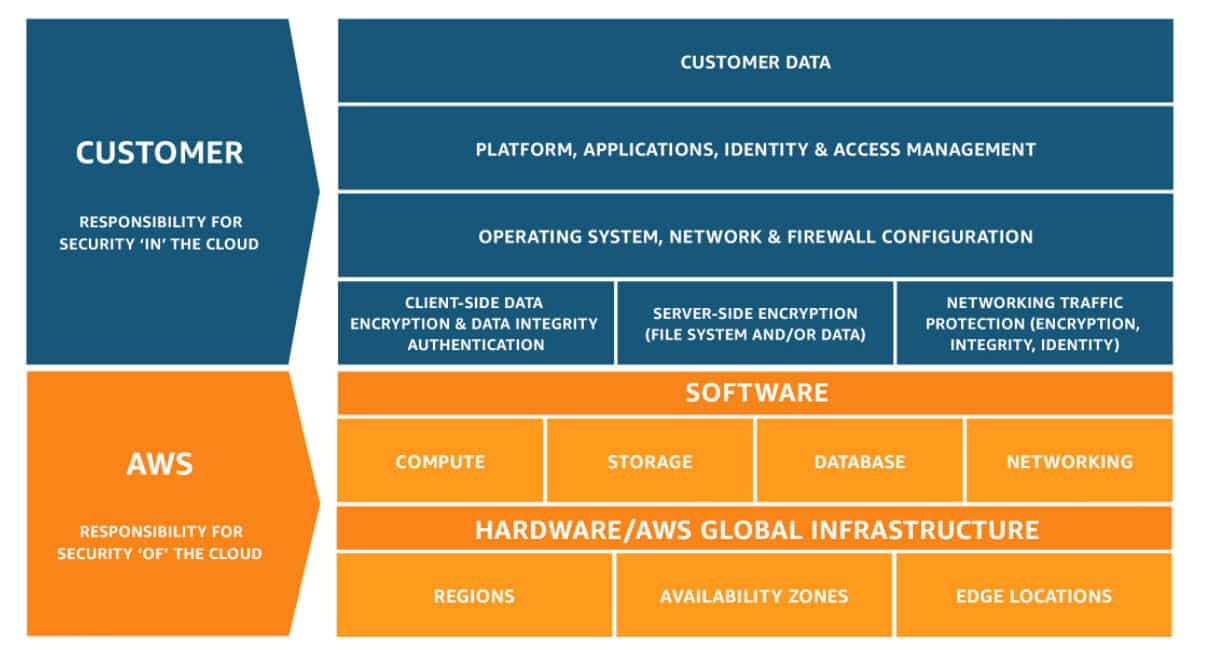
03- AWS’s Shared Responsibility Model for Cloud Compliance | Security Analytics
Amazon functions under a shared responsibility model like many cloud suppliers. It takes control of its infrastructure’s security and that’s why it has made platform security concern for the protection of customers’ critical application and information. Detection of abuse and fraud in made possible via Amazon, it notifies customers as well by responding to incidents. However, the clients are also responsible to ensure that data is secured i.e. it is not shared with the company either inside or outside along with the security of their AWS environment configuration. Furthermore, they are accountable to enforce governance and compliance policies and identify the misuse of AWS by its user.
The responsibility of Amazon towards Cloud Compliance | Security Analytics:
Since Amazon has less authority over the use of AWS by its customers, it is mainly concerned about the AWS infrastructure’s security that includes the protection of its networking, computing, storage, and database anti-intrusion program. The prime concern of the Amazon is the security of the hardware, software and physical amenities that give the services of AWS. It is responsible for the security configuration of Amazon DynamoDB, Redshift, RDS, Workspace and Elastic MapReduce, etc.
The responsibility of the customer towards Cloud Compliance | Security Analytics:
The customers of AWS have the responsibility for the secure use of unmanaged services of AWS. For instance, when Amazon has created numerous layers of security features for the prevention of unauthentic access to AWS that includes multifactor authorization, it is customer’s responsibility to ensure that multifactor authorization is turned on for its users, mainly for those users that have the most substantial IAM permissions in AWS.
04 – Data storage and AWS Database Services
The latest incident of AWS data leaks created by misconfigured S3 Buckets has highlighted the requirement to ensure that AWS services of data storage are always maintained safely. Amazon provides various database services to its users such as Aurora (MySQL relational DB), Amazon RDS (relational DB), Redshift (petabyte-scale data warehouse), DynamoDB (NoSQL DB), and ElastiCache (in-memory cache). It offers data storage with S3 and Elastic Block Store services as well. Some best practices of data storage and AWS database security are dropping below:
- Make sure that no S3 Buckets are writeable or readable publicly until it is needed by the business.
- To help post-incident argumentative inquiries and auditing for a particular database, toggle on the audit logging of Redshift.
- Encrypt data which is stored as an added security layer in EBS.
- Amazon RDS encryption as an added security layer is a must.
- To reduce the chances of a man-in-the-middle attack, allow requiring SSL parameter in all the clusters of Redshift.
- Securely connect to RDS instances for minimizing the chances of malevolent activities for instance attacks by brute force, SQL injections or attacks by DoS.
05 – Bastion Login for Each AZ
Bastion host a separate EC2 instance that runs within a VPC and it is peered – also called “Jump Server”. For this purpose, you are required to have replicated networks in each zone. Secured Bastion logs in host to facilitate command-line Secure Shell (SSH) access to Amazon EC2 instances for system administration and troubleshooting privileges and maintenance. Make sure that you do not log into EC2 directly. It holds significance to minimize blast radius. For example, consider you have one Bastion host that is going to all of your zones which depicts that it is compromised. It means that every single zone is compromised. So, in this way, if one zone is compromised, you can shut that down and the other zone can take over as a high availability zone. Thus, you can keep your services going while you clean up the compromised zone. To avoid AWS account VPC peering is highly preferable. It is basically controlled testing in our environment for Cloud Compliance | Security Analytics.

06 – AMI
Amazon Machine Image is a pre-built set of stacks and provides the information required to launch an instance which is a virtual server in the Amazon Elastic compute cloud (EC2). These instances are completely managed by the customers so their security falls onto them. Therefore, make certain that you disable password-only access to the host that uses SSH keys and disable remote “root” account log-ins. And ensure that only required applications and services are enabled. It is a fact that most of the customers are not intended to do OS hardening, particularly around their allies. There are tools within AWS that can assist you to organize it with excellence.
07 – CloudWatch
It is a monitoring service for the cloud resources and the application of AWS. With Amazon CloudWatch, you are allowed to track and collect metrics, monitor and assemble log files, set alarms and respond to changes in your AWS resources automatically. It is capable of monitoring AWS resources, for instance, Amazon DynamoDB tables, Amazon EC2 instances, Amazon RDS DB instances and custom metrics produced by your services and applications as well as any log files generated by your applications. You can leverage Amazon CloudWatch to acquire system-wide visibility into the utilization of the resource, operational health, and application functionality. These insights are vital for Cloud Compliance | Security Analytics and operating your application efficiently.
Significances:
- Amazon EC2 Monitoring
You can view metrics to utilize CPU, disk utilization activity from EC2 instances of Amazon and data transfer with no extra charges. The Amazon CloudWatch delivers comprehensive monitoring for EC2 instances that has metric aggregation and higher resolution. And the most attractive attribute of this software is no complimentary software is required to install for Cloud Compliance | Security Analytics.
- Monitor Custom Metrics
Submitting Custom Metrics that are produced by your applications by a simple API request and are monitored by Amazon CloudWatch is an amazing feature of Amazon CloudWatch. You can store and send metrics that are vital to the operational performance of your applications. It aids you to spot trends and troubleshoot to enhance Cloud Compliance | Security Analytics.
- Store and Monitor Logs
The CloudWatch permits you to troubleshoot and monitor your applications and systems while using your current application, system and custom log files. And you can easily send these to CloudWatch Logs to monitor them in real-time. This will eventually help you to operate and understand your applications and system better. With this software, you can store your logs by using low-cost and highly durable storage for further access.
Cloudnosys platform delivers security, compliance, and DevOps automation. Continually scan your entire AWS services for security and compliance violations for Network Security, IAM Policies, VPC, S3, Cloudtrail etc. Provides DevOps automation and policy driven guided remediation for Azure and AWS. Meet PCI, HIPAA, NIST, ISO27001, SOC2, FISMA, AWS CIS Benchmark compliance quickly.
CloudEye
Cloud Eye is a multidimensional monitoring network for the resource. CloudEye can be used to control service resource utilization, track the operating status of cloud services, configure alarm notifications and rules, and respond quickly to resource changes.
Benefits:
- Real-Time Monitoring:
CloudEye captures real-time data from cloud providers via a secure direct connect and sends alerts immediately when risks are observed with your infrastructure.
- Easy to use:
Dashbaords and recommendation engine shows you what to take action now and helps you remediate with detailed instructions.
- Numerous Notification Types:
CloudEye sends slack messages or emails for notifying users about the alarms that are produced.
EagleEye
It is a cloud-based Security software that provides unparalleled workability, security, accountability, and flexibility. The EagleEye is specifically designed for the Cloud community.
Key Takeaways:
- real time Thread Detection
- Policy Guardrails for your cloud
- Monitor changes and analyzes risks in real time.
- Protects your application, data and infrastructure including your IAM security groups.
Conclusions
Building Cloud Compliance and Security Analytics togetheris one step ahead to efficiency and ease for leading your business to success with great security psoture. As it enhances collaboration, gives unified access to data, and provides agility and scalability for well-managed business activities.