What You Need to Know About The Growing Importance of CSPM
In today’s fast-evolving digital landscape, where remote work and multi-cloud strategies have become the norm, safeguarding your digital assets is more critical than ever. Cloud


In today’s fast-evolving digital landscape, where remote work and multi-cloud strategies have become the norm, safeguarding your digital assets is more critical than ever. Cloud

The dynamic nature of cloud computing brings immense opportunities and unique challenges. Businesses increasingly leverage the cloud for flexibility and scalability, but ensuring robust cloud

Cloud computing has revolutionized how businesses operate, offering scalability, flexibility, and cost efficiency. But with these benefits come new challenges—most notably, the rise in cyber

In today’s digital landscape, where businesses heavily rely on cloud computing, ensuring the security and compliance of cloud environments has become a top priority. Cloud

Application Security is one of the core aspects of cyber security which is not getting the attention it deserves. Many developers tend to focus on

Customers are used to being able to use a lot of internet tools within their environment. They have a lot of security controls. We have

“The number of connected devices means potential vulnerabilities and insecure end-points are growing exponentially”- Johan Paulsson, CTO, Axis Communications With the growing inclination of organizations

Moving your company to the cloud for gaining speed, flexibility, and better customer experience is a smart digital move. In this regard, your developers are

[st_row][st_column][st_text ]With the world moving towards cloud, options like online data are becoming increasingly popular. Owing to their storage being easily accessible, and scalable. Especially

Prediction of cybercrime related losses by the end of 2019 stand at a staggering $6 trillion. Bypassing effective compliance with cybersecurity guidelines can put a
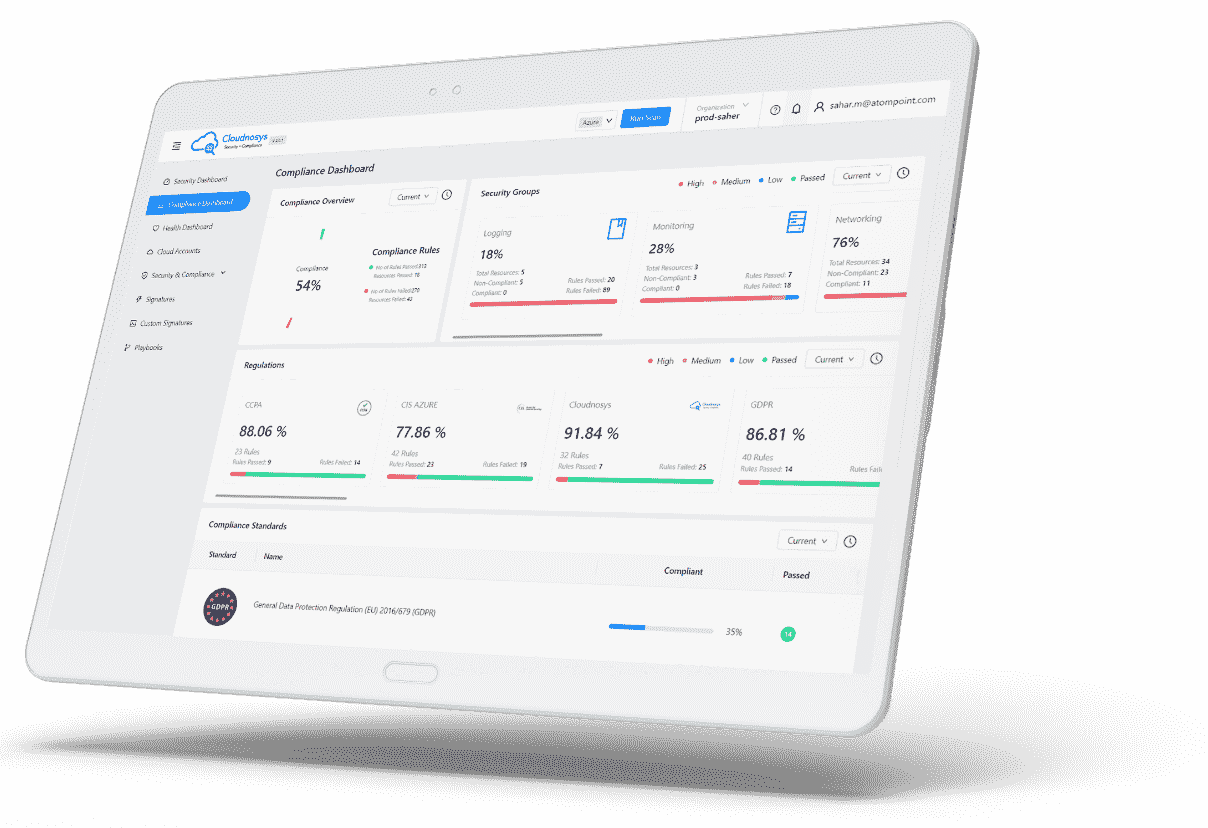
Stay updated with all that you really want to get aware of in cloud security and our most recent researches.