Prediction of cybercrime related losses by the end of 2019 stand at a staggering $6 trillion. Bypassing effective compliance with cybersecurity guidelines can put a lot of entities at risk.
Introduction
Steve Jobs was one of the greatest pioneers of the 20th century. He said: “I don’t need a hard disk in my computer if I can get to the server faster. Carrying around these non-connected computers is byzantine by comparison.” There is a reason 83% of enterprise workloads are going to be on cloud by 2020, and it is resource optimization across all departments. According to Gartner more than 50% of US Companies will be using NIST as the baseline for their security posture. President Trump has issued execute order in 2018 that says all Federal Agencies should comply with NIST compliance and security standards.
Cloud computing is a $182.4 billion market that is growing by 17.5% each year. The leading factor driving more and more public cloud adoption is digitally transforming enterprises. Despite the acceptance rates, however, 66% of IT professionals still say cybersecurity is their biggest concern when adopting an enterprise-level cloud computing strategy. With lack of Cloud Cyber Security professionals, more and more companies are relying on commercial, off the shelf security products and services to race to a secure cloud. Cloudnosys provides complete end to end cloud security solutions that can strengthen your Cloud infrastructure for NIST 800-53, 171 FISMA high Controls and more such as ISO 27001 security model.
The Importance of NIST Compliance for the Cloud
The National Institute of Standards and Technology is a government agency with non-regulatory authority that provides framework for the organization in the fields of science and technology. NIST Compliance is mandatory under the Office of Management and Budget policies. It helps organizations establish better check and balance, especially to prevent cybercrime.
NIST Cybersecurity Framework is one of the most widely accepted compliance schedules that outline best practices for federal agencies. In this article, we will take a look at different aspects of NIST Compliance. The requirements, benefits, and guidelines that can ensure effective implementation of the NIST regulations will be discussed.
The requirements of NIST Compliance
NIST provides a variety of guidelines that include best practices for a variety of domains in a host of fields. For instance, it has a set of guidelines that help federal agencies meet necessary requirements in the Federal Information Security Management Act or FISMA. The reason companies comply with NIST framework is because they ultimately help the organization meet other acts and ordinances like HIPAA and SOX etc.
Chief among the NIST compliance regulations is the 800 series which describes the security policies and
requirements for US Federal agency information systems. It helps prioritize cyber assets, pin point the thresholds for potential risks and determine the optimal way of reporting any suspicious activity to authorities.
The NIST SP 800 series has a number of sub-clauses. The NIST SP 800-53 gives a framework for security controls that are required by federal systems. The NIST SP 800-37 aids in promoting continuous monitoring of controls given in 800-53 to ensure real-time risk management. The latest in the list is the Draft Special Publication 800-171.
This document plays a role in clarifying what third parties should do in case of data breach. It applies to non-federal entities like private sector firms that store sensitive federal information. These regulations protect Controlled Unclassified Information or CUI which is housed in computers or information systems of organizations outside the federal government.
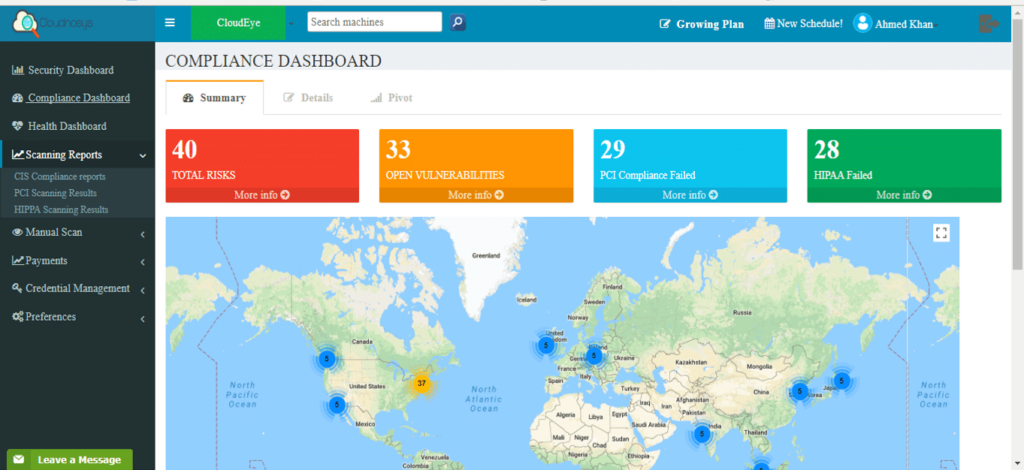
The following are the 14 categories of security requirements that have to be met by companies looking to implement the NIST Compliance of SP 800-171 guidelines. Under each category, there are distinct policy tests which should be met by the database or program under review. All these addresses are an integral part of ensuring security of CUI, and together, form a holistic system. Cloudnosys CloudEye platform can scan your cloud and monitor for these violations in the categories below:
- Access Control: Broken down into two types, i.e. basic and derived security requirements. The guidelines here include limiting system access, controlling the flow of CUI and employing principles of least privilege.
- Awareness and Training: The basic requirements include making managers and users aware while the derived requirements focus on providing training on recognizing and reporting potential threats.
- Audit and Accountability: Under this requirement, organizations have to create and retain system audit logs, ensure that individual actions in the information system can be traced, protect audit record information from deletion and modification, etc.
- Configuration Management: To comply with this, organizations have to establish, enforce and maintain baseline configurations for security as well as inventories of organizational systems. The derived requirements include tracking and reviewing log changes along with control user-installed software in systems
- Identification and Authentication: Companies must identify and authenticate user processes and devices. They must put in place multi-factor authentication practices and implement some strict password controls
- Incident Response: Establishing and testing incidence response capabilities fall under this category
- Maintenance: Includes maintaining organizational systems, promoting controls on tools, ensuring any equipment taken off-site is sanitized of any CUI and supervise maintenance activities with authorized personnel
- Media Protection: Limit access to CUI, destroy any media containing CUI before disposal, prohibit use of portable storage and protect the confidentiality of backup, etc.
- Personnel Security: Screen individuals prior to authorization and ensure CUI is protected from physical access by personnel after their transfer or termination
- Physical Protection: Protect against and monitor physical facilities, escort visitors and enforce safeguarding measures
- Risk Assessment: Periodically asses risk to operations, scan for vulnerabilities and remediate them effectively
- Security Assessment: Assess security controls regularly, design and implement plans to correct deficiencies and monitor security controls, etc.
- System and Communications Protection: Employ system engineering principles, software development techniques, and architectural designs as well as separate user functionality from system management ones
- System and Information Integrity: Identify, report and correct flaws in the system, update malicious code protection practices and perform periodic scans, etc.
What benefits does NIST Compliance bring?
The NIST compliance frameworks are extensive because they are set out after a thorough analysis of several security documents, test cases, organizational reports, and publications. They receive regular updates that keep them relevant for various practices like evolving cybercrime activities. The most noteworthy benefits of implementing NIST regulations are given below:
Secure internal and external infrastructure
First and foremost, the NIST Compliance framework is directed towards establishing superior cybersecurity for organizations. The principles and guidelines come from thousands of professionals and years of research in the field. It also encourages the organization to accept an adaptive and proactive approach towards an audit of compliance requirements.
NIST monitoring and compliance creates a ripple effect across departments within an organization as well as among external stakeholders like vendors and distributors. NIST compliance audit requires individuals and other organizations associated with the company to fall in-line with the regulations too. As a result, more comprehensive security infrastructure is put in place. For AWS, Azure and GCP Clouds, it requires a level of expertise to interpret these regulations and create the automations to test these controls.
Eliminating cybersecurity vulnerabilities
Among the 14 categories of NIST SP 800-171 compliance requirements are tests that act as barometers to identify the level of vulnerability that an organization has. This is another benefit of NIST monitoring, that it helps organizations point out areas of cybersecurity in which they lag so they can put the necessary steps in place to plug these loopholes.
According to a report by Cybersecurity Ventures, currently there are no companies that are 100% compliant. Companies are only implementing about 39% of the controls, giving rise to some of the major difficulties in the industry. It is loopholes like these that need to be addressed for NIST compliance to take effect in full force.
Foundation for compliance with other frameworks like HIPAA and FISMA
The NIST compliance framework doesn’t work alone. They work in sync with and sometimes serve as foundations for a number of other regulatory clauses like FISMA and HIPAA. Being compliant with NIST SP 800-171 also allows organizations to be in a better position to accept newer regulations, as they come out. Examples of these include the NYDFS 23, NYCR 500 and Model Law from the insurance industry that uses NIST SP as a foundation. Cloudnosys has created a cross map between these regulations for all public cloud like AWS, Azure and GCP.
It is important to be aware of the fact; and NIST regulations themselves highlight this too; that being compliant doesn’t mean fool-proof cybersecurity. This is the reason why NIST compliance guidelines begin by stating that organizations should account for their cyber-assets using a value-based approach, and then move to find the most appropriate ways of prioritizing cybersecurity around the crucial ones.
NIST SP 800-171 Compliance
Embracing NIST compliance is a start down the most effective path to complete cybersecurity. The process may be long and cumbersome for companies who are just beginning with a NIST compliance framework. It can be made simple using a simple approach which involves a few basic questions.
First and foremost, these queries are about whether the CUI scope is covered, secondly, is the CUI isolated, third, how and whether the CUI is controlled, and lastly, whether the organization has mature IT practices or not. If the company offers a negative response to any of these questions, then they can begin NIST compliance efforts through the following steps:
Identify loopholes and shortcomings
Depending on the various controls and tests given under different categories, companies can determine their current outlook with regards to NIST SP 800-171. The most commonly skipped NIST guidelines are related to CUI flow, session termination, audit logging failure, configuration, black and whitelisting, test incident response and CUI access, etc.
A NIST compliance audit can help shed light on matters where the cybersecurity infrastructure of a company is not how it should be, with regards to NIST SP 800-171. This can serve as a stepping stone to progress.
Determine your own knowledge about NIST
The Cybersecurity Ventures report that came under discussion earlier clearly states, that the biggest reason for non-compliance to NIST guidelines on such a wide scale is the fact, that, more than half of the organizations under review found regulations hard to understand. While this can be a point of concern, it doesn’t serve as a good enough excuse to forego implementation completely.
This is why the second step in becoming compliant involves testing how much of the NIST guidelines an organization and its executives can comprehend. Without a clear understanding, the implementation will become a one-off practice to pass stringent check and balance that would come otherwise.
Contact an experienced organization to handle the task for you
Many times, ensuring NIST compliance requires the help of a professional Cloud expert, who understands the regulations and can interpret them in a way that can help the layman learn them too. Never hesitate to make an investment in a professional service provider who can handle effective implementation of the NIST compliance framework for you.
The Ultimate Solution – CLOUDNOSYS
Imagine not having to read or understand long lists of detailed regulations. Most of the times, business people aren’t technical experts. They are more of laymen, trying to improve their business infrastructure.
You and I could be one of them. In this day and age, we all need cloud infrastructure no matter our area of expertise, While people with in depth knowledge of IT might not have a hard time understanding these regulations, other businessmen will struggle to grasp the concept of each law.
Trying to understand the technical jargon thrown in there, with so many concepts and theory that we have no clue about, can be quite troublesome a task. Moreover, hardly anyone has time to read hundreds of lengthy rules thoroughly. Even IT professionals might not want to go through with having to read a large, black and white document written in formal language.
As if that wasn’t enough, you have to align your entire business infrastructure with the regulations to ensure compliance too. Which means having to check each of your operations down to the grassroots level, and look at every file related to your business in order to detect threats or check compliance.
If you have a running business, you are well aware of the fact that this is no piece of cake. Your data is increasing at a great speed, and you have a lot of other things to manage as well.
Wouldn’t it be great if there was a service that did it for you? Something that was quick, efficient and worked well in general? A system you could rely on at all times?
That’s where CLOUDNOSYS has you covered. CLOUDNOSYS offers automated systems that scan your entire business on cloud including operations, data and files to check compliance. It detects threats and vulnerabilities as well. It can even resolve many issues by itself using dynamic automations that can remediate your violations.
CLOUDNOSYS has automated software’s that not only check compliance, but report back in comprehensive and visually appealing ways, with risk ratings giving you a complete security posture. We reduce alert fatigue through automation and self-analysis. We highlight the exact areas that need your attention and tell you exactly why and how to fix it with step by step instructions
CLOUDNOSYS gives a bird-eye view of all your risks in compliance and security of your business. Having your entire business at your fingertips, without having to worry about compliance and issues is next level privilege. Worried about what happens if there’s an update in rules? The software will update itself.
Now you can focus on more important things when the basic challenges are taken care of. This means you can explore more opportunities, make better decisions, and achieve new heights of success. This automated software is a steppingstone for your business.
This can leverage your business and help you expand it. You can scale your setup to give better returns on investment. It makes your business easy and manageable.
You can get a 14 day free trial of CLOUDNOSYS. It will give you an idea of how it manages to set you free from all the troubles regarding compliance.
There’s nothing to lose in a free trial now is there?
Conclusion
NIST compliance frameworks create an efficient foundation for creating secure cyberspaces, especially in the cloud. Cloudnosys provides a Security compliance audit, reporting and real time monitoring platform to keep companies NIST compliant for their AWS, Azure and GCP Clouds, and reduce complexities. Businesses are rapidly moving towards cloud computing and with a growing fear of cybercrimes. NIST compliance provides a solution to major security threats and keeps a strong hygiene in controlling security for the cloud. Organizations must review and update their entire cloud footprint to NIST compliant clouds so that sensitive data can be kept secure everytime. Cloudnosys provides cloud security, compliance reporting and monitoring solutions to drive compliance through automation.