Cyber security, especially ransomware, has been a big challenge across the globe. Gartner predicts that 75% of CEOs will be personally liable for cyber-physical security incidents by 2024. The best we can do is as we find bugs we fix them. But these security vulnerabilities can be exploited. There are large groups of malicious actors out there that are constantly scanning, viewing code, looking for vulnerabilities, and the ability to access systems. I implore you, learn about ransomware. Learn how to protect yourself against it.
How Ransomware Attacks and How Does it Spread?
Let’s quickly dive into how ransomware attacks and how it spreads in an environment. In most situations, it all begins with a click on an attachment in an email or a website that downloads malware on your laptop. The malware then tries to move literally to other servers in the network. It can be a remote desktop attack possibly through a vulnerability and software as well. It looks for unpatched systems, cached or leaked passwords, and gets into more critical systems. At some point, it applies a ransomware encryption lock on the data. When you access the data it throws up a ransom note. Sometimes it even locks the backups, which can not be restored.
How Google Cloud, AWS, and Azure Protect from Ransomware?
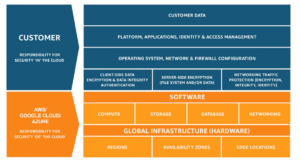
To protect ourselves from this and other types of malware, we have built multiple layers of protection, most of which are automated and available to customers by default. These cloud computing platforms help protect by their global visibility into malicious sites and make detection highly effective. If you are a Gmail user it prevents thousands of malicious attachments from ever reaching inboxes. Even if it reaches inboxes, Google Safe browsing in Chrome browser protects users by identifying dangerous links and emails and shows warnings if users click on them. This stops access to any websites which are known to distribute malware. In Google Drive, all files undergo a malware scan prior to any download or sharing. It prevents ransomware from propagating.
Applications are sandboxed to prevent harm to the host machine. Often these features remove any need for anti-malware or antivirus software. AWS is also responsible for the security of the cloud and protecting the infrastructure. But these cloud computing platforms are not responsible for security in the cloud. It’s the customer’s responsibility. This is where Cloudnosys helps the customer. Protect your cloud infrastructure from security threats, data loss, and compliance risks with real-time continuous monitoring, auditing, and automated remediation with our Cloudnosys Security Platform. We provide a combination of fully integrated Cloud Infrastructure protection, governance, and risk management with automated Playbooks. Centralize all security findings, prioritize and enrich alerts, and remediate threats faster via automation through our playbooks feature. It’s a shared responsibility.
Ransomware Protection and Recovery
There are many strategies for ransomware protection and recovery in the interest of time today, I’m going to focus on the top 10 today that would be helpful for you all.
Protect laptops and desktops
Use products to detect and stop malware. Use cybersecurity platforms. Our platform Cloudnosys is one of these as well which can help you stop data breaches.
Patch your systems ASAP
Use tools that can identify which servers have security vulnerabilities. Then you need automated testing and tools to patch those servers. If organizations can keep their systems patched ransomware will not be able to target the servers. AWS patch manager can help with this.
Use immutable instances
Use immutable instances that are very short-lived. Test and patch an AMI template and then use these templates to launch immutable instances to get out of the patching production instances.
Use AWS Managed DB, File, and Analytics services
Reduce time and avoid the burden of managing and patching mission-critical databases and file servers by considering storing data in a fully managed data store. You can use Amazon DynamoDB, Amazon Elastic File System any many more for this.
Automate least privilege policies
Malware extracts the cached or stolen passwords and uses them to gain access and spread ransomware so we need to set up the least privileged policies for users. To improve your security posture, you can use an automated least privilege policy, for determining which users and roles need which API permissions. This helps you avoid the hassle of granting privileges to thousands of users.
Fence everything
Consider building fences for your various applications using different accounts and IDs or different VPCs. You could have servers in public and private subnets. Use security groups to limit communication from and to specific IP addresses and ports. Enable VPC Flow Logs to detect anomalous traffic to an IP.
Manage all firewalls centrally
Use a web application firewall to avoid exploits from attackers. Inspect and filter all the traffic.
Automated anomaly detection at scale
Something that has never been done before is an anomaly. Anomalies are unusual behaviors or attempts that must be detected in near real-time and more importantly, an action must be taken automatically.
Data Protection
Use mechanisms so that data can only be allowed to get accessed only from within your VPC and not from the public internet. Also, use encryption at rest. Keep critical apps backed up to recover from a previous point in time. Replicate backups.
Hybrid Cloud
Automate patch management at scale using tools for your on-premises workloads. Use machine learning to detect anomalies in near real-time. Make backups immutable so that an internal bad actor will not be able to delete those backups so that you should be able to do recoveries.
Ransomware knows no boundaries. Companies are vulnerable to Ransomware through many different attack vectors. So to summarize, consider a zero-trust approach for ransomware protection and recovery. The impact of ransomware is massive. Research shows cyber thieves have made at least $25 million from Ransomware and this is expected to grow. You are equally vulnerable to it on a home PC as a corporate internet is on their internet. NIST is a great framework. Some of the ways that companies can mitigate the risks of an attack are by having proper firewalls in place, having content filtering inside of their network, properly securing their infrastructure with a tested and proven anti-virus, and some content filtering on the web.