Note: It may take 2-3 mins to deploy the IAM roles stack for the Basic protection level and for the Advanced protection level another 4-5 mins will be added to deploy 3 more stacksets. Cloudxray will be deployed with the latter.
1. Introduction #
In this guide, we cover our available deployment types to protect your cloud accounts. Cloudnosys is offering Basic and Advanced modes of deployment. The Basic protection level will provide just the misconfigurations detection whereas the Advanced protection level will provide Malware detection, OS vulnerabilities, and real-time Monitoring as well.
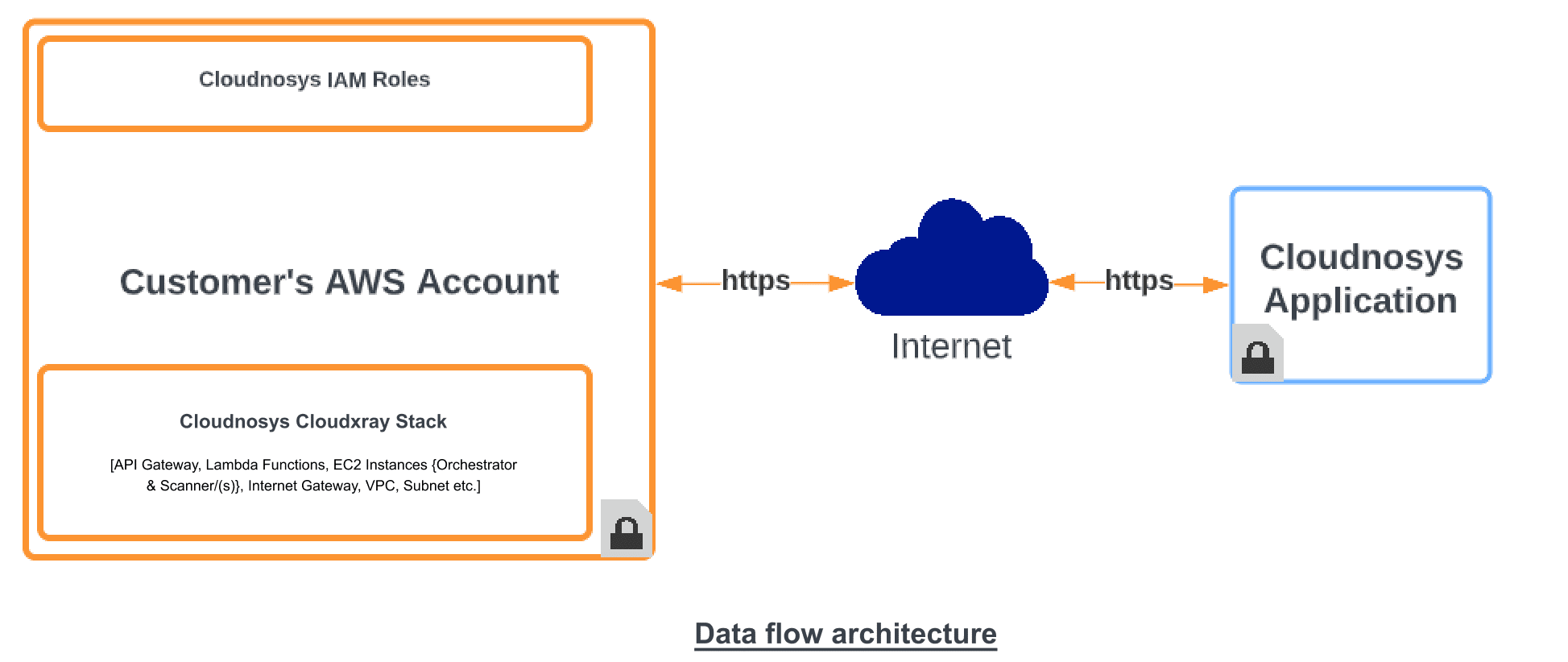
Cloudxray architecture has two major components: Orchestrator & Scanner. Orchestrator has a single-region deployment whereas scanner/(s) will be deployed in all the discovered regions with instances to scan. During the Cloudxray deployment, you will be asked to select a region, using a drop-down list, to spin up Orchestrator. Scanning instances will be automatically provisioned depending upon the discovery of EC2 instances to scan, in your cloud account. Hence, the solution (Orchestrator) should ONLY be deployed in one region, where StackSet deployment is offered by AWS.
Note: Cloudxray scanning is supported in all the regions enabled in the customer’s AWS cloud account however deployment of Cloudxray is ONLY supported in regions, where StackSets are supported
Caution: When adding the AWS cloud account on Cloudnosys (Advanced protection level), please ensure that you are not reaching the limits of AWS services quotas in the region you are looking to deploy the resources. This will help you avoid the failure of AWS CloudFormation template deployment. (Please find the list of resources that the AWS CloudFormation template will deploy, under section 3 – ‘Architecture’)
Recommendation: Cloudnosys recommends the Advanced mode of deployment since this will give you an additional protection level for CVEs (malware) & OS Vulnerabilities together with the coverage of risks and vulnerabilities in your AWS account, through our Agentless Cloudxray and EagleEye (real-time detection) features.
2. Prerequisites & Requirements #
In this section, we detail the prerequisites and requirements to run and operate our solution.
Cloudnosys supports malware detection and posture management (misconfiguration detection) of Linux, Windows, and Mac. Vulnerability scanning (CVE) is currently supported on Linux-based operating systems only.
2.1 Time to Deploy Cloudxray #
The deployment will take about 2-3 minutes for the Basic Protection Level. For the Advanced Protection Level, an additional 4-5 minutes may be taken. Lastly, configuration and testing could take 3-4 minutes.
2.2 AWS Account #
You must have an AWS account set up already. If you don’t, we recommend that you visit the following site and set up an account first: https://aws.amazon.com/getting-started/
2.3 AWS Identity & Access Management (IAM) #
Your IAM user should have a policy that allows AWS CloudFormation actions. Do not use your root account to deploy the CloudFormation template. In addition to AWS CloudFormation actions, IAM users who create or delete stacks will also require additional permissions that depend on the stack template. We recommend you make sure that your AWS console user for stack deployment has Administrator privileges so that the operation will be performed without any failure.
Note: Cloud Administrator should have a sufficient depth of knowledge to deploy the resources specified in this guide
3. Architecture #
Cloudxray will require some resources to be deployed in your AWS account. Firstly, when you onboard your AWS cloud account onto Cloudnosys, you will be asked to create roles (AdministrationRole, ExecutionRole, and Cloudnosys Misconfigurations Detection Role). Once the roles are deployed, you will proceed to the deployment of the Cloudxray Stack. The Cloudxray Stack will deploy the following resources in your AWS account:
|
Resource |
Type |
Purpose |
|
|
1 |
VPC |
Permanent |
A virtual private cloud where all the Cloudxray resources are provisioned |
|
2 |
IGW |
Permanent |
Internet Gateway to attach with the VPC for internet access, required to update definitions of viruses |
|
3 |
Subnet |
Permanent |
A public subnet in the VPC |
|
4 |
EC2 |
Permanent |
Orchestrator Instance for orchestration of Cloudxray |
|
5 |
Scanning Instances |
On-demand |
Scanning Instance which will be provisioned when the scan is started, so that the volumes will be attached to this instance for scanning |
|
6 |
REST API |
Permanent |
API gateway to authorize the incoming requests and proxy them to the Request Receiver Lambda |
|
7 |
API Gateway Authorizer |
Permanent |
Authorizes incoming requests by forwarding them to the Authorizer Lambda |
|
8 |
Lambda (Authorizer) |
Permanent |
Checks for the correct authorization code and allows or denies the request |
|
9 |
Lambda (Receiver) |
Permanent |
Request Reciever Lambda to proxy requests to the orchestrator EC2 |
|
10 |
Lambda (Forwarder) |
Permanent |
Will receive data from the Orchestrator and forward it to Cloudnosys Platform |
|
11 |
SG1 (Orchestrator SG) |
Permanent |
Security Group attached to the Orchestrator which will only receive requests from Request Reciever Lambda Security Group |
|
12 |
SG2 (Scanner SG) |
Permanent |
Security Group attached to the Scanning Instance which will only receive requests from Orchestrator Security Group |
|
13 |
SG3 (Reciever Lambda SG) |
Permanent |
Has rules to block all incoming requests. No outgoing rules defined |
|
14 |
SG4 (Forwarder Lambda SG) |
Permanent |
Allow incoming requests from Orchestrator SG. Outgoing open to all |
On every scan, Cloudxray will discover the instances and launch the scanning instance/(s) in the discovered regions to scan the volumes within their own region. After the scan is completed, the snapshots and volumes, created for scanning, will be deleted through our Cleanup Operation.
4. Security #
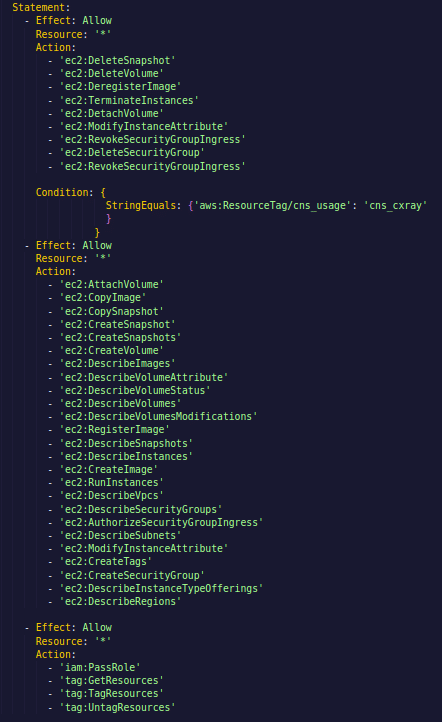
The CloudFormation template creates a service-linked IAM role “orch-instance-profile” that attaches with the EC2 instance (Orchestrator) and allows the Orchestrator to initiate AMIs creation/deletion, Snapshots creation/deletion, volumes creation/deletion, decrypt the encrypted volumes using KMS keys, and creation/removal of security group rules on orchestrator, as per need. After we decrypt the encrypted volume, we re-encrypt the copied volume with our keys, immediately. We also encrypt data at rest and in transit within this architecture.
The trust policy associated with this IAM role, allows the Orchestrator to assume the role. The inline embedded policy of the role provides limited access to perform the required tasks like modifying, terminating, deregistering, detaching, revoking, deleting, etc.
In your environment, Cloudnosys will ONLY be able to delete the resources that get created by Cloudnosys itself. Our fine-grained access policy of the instance profile role will make sure that this will be the case (please review the policy snippet above).
Note: Cloudxray deployment neither requires root privileges nor the operation requires it. Do NOT use your root account to deploy the CloudFormation template. We recommend you create and use a new user with Administrator privileges so that the operation will be performed without any failure.
5. Cost #
- Scanning 25 GB of data for 1 hour will cost $0.19 (t2.xlarge running cost).
- The cost for scanning 1 GB of data is $0.0079.
- For scanning 100 GB of data, the cost will be $0.76.
- The estimated cost for scanning 1 TB of data is $7.6.
NOTE: As the number of instances increases, the cost of Cloudxray will be more optimized as 5 volumes can be scanned by one scanner at a time.
Please visit AWS Pricing for the latest pricing information.
6. Deployment Assets #
The CloudFormation template will deploy two types of assets in your (client’s) AWS environment:
- On-demand Assets
- Standard Assets
On-demand Assets include the number of scanning instances, depending upon the discovered instances in your AWS accounts. One scanning instance can cater to 5 EC2 instances for scanning. The snapshots of the volumes attached in all the discovered EC2 instances are created, thereby creating AMIs from the snapshots to get the volumes attached with each of the EC2 instances, to perform the scanning. For example, if you have 50 instances, then the number of scanning instances will be 10, to perform scanning.
Standard Assets include the resources that are permanently deployed in your (client’s) AWS environment through the AWS CloudFormation template, required to perform the orchestration and virus definition updates of the agentless scanning system. The list of the provisioned assets will be as follows:
- VPC
- Public Subnet
- Internet Gateway
- Instance Profile IAM Role
- EC2 Instance (Orchestrator)
- Rest API deployed on API Gateway
- Lambda Functions
7. Monitoring (Health Check) #
To make sure that the application is functioning normally, the following steps can be taken:
- You will receive email and platform system notifications if there’s an issue detected in the system
- You can check logs (AWS/Azure/GCP) for any errors generated by Cloudnosys deployed resources
- Check to see if the last scanned date is NOT older than expected.
8. Maintenance #
Routine Maintenance: Cloudxray is required to be redeployed via the AWS CloudFormation template when there is an architectural change. For that, the Cloudnosys team will notify you and provide an updated AWS CloudFormation template with instructions. Other components within Cloudxray such as virus definitions are auto-updated through trusted sources.
Emergency Maintenance: In case of an emergency with respect to the functioning of Cloudxray, you may need to get in touch with our support team via email at [email protected], and your account manager will make the arrangements to get it fixed for you ASAP.
9. Support #
Cloudnosys is a SaaS solution and is self-servicing. However, our enterprise package comes with 4 weeks of onboarding & training. For all other matters, assistance is available via live chat on the platform or via email at [email protected].